I will be live-blogging all about the latest dark web happenings from the show starting tomorrow. Gordon G. Chang, the author of Nuclear Showdown: North Korea Takes On the World as well as other works is about to take the stage here at the Inside Dark Web Conference.
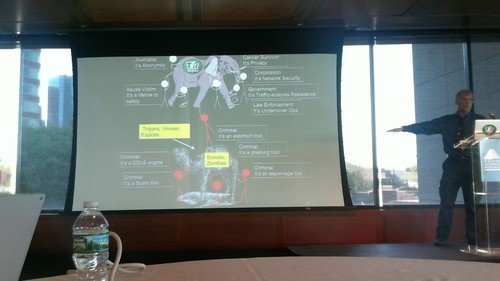
The most dangerous criminals on the Dark Web are states. Hackers sponsored by Russia attacked Ukraine in the past. It is also a matter of time before a rogue state or bad actor takes out critical infrastructure in the US. In addition, he says some believe the Chinese are behind the great blackouts in the US last decade.
He then discuss the Bowman Avenue Damn in Rye Brook and how the Iranian National Guard was responsible. He also mentioned how Wells Fargo and JP Morgan Chase were also attacked.
Hackers he said will go after American businesses as well as governments.
He said the attacker who went after OPM and took over 21M government worker names and their details also went after Anthem, United and almost ten other companies.
He said the FBI does now issue warning against Chinese hacking (one, earlier this May) – when they did not do this before. He said that multiple agencies have sounded the alarm about APT6 – an allegedly Chinese Nation-state sponsored hacking group.
Some believe this group has been operating since 2008 or 2011. He also said President Obama met with Chinese leaders and agreed neither country would hack for commercial purposes.
He went on to say FireEye noted that numerous Chinese hacking groups have ceased hacking as a result.
He says experts say that the attacks are still coming but China is using better “trade craft.”
He said in past days, the Chinese would show the data they stole.
In addition, Silicon Valley is working more closely with the government to identify attacks and attackers.
He said there is no cost on China for taking hundreds of billions of dollars per year of American Intellectual property – in the form of US exports to Asia.
Others say hacking costs us companies $400B per year and China is responsible for 90% of this number or $360 billion.
Others say this will continue until we demand that it stop.
At the moment “There is very little reason for Beijing to stop what it is doing.”
He went on to say that some time back five Chinese hackers were indicted but it is unlikely we will never find them and bring them to justice.
At this point, companies are not allowed to fight back.
Some are suggesting US companies be given the right to do this.
Others say, until hacking stops, we need across the board tariffs on Chinese products. Obviously Donald Trump believes this and Senator John McCain agrees.
In addition, other countries see China is not being held liable and other countries could copy the same path to economic prosperity.
“China wants to move up the value chain in manufacturing and they cant do this unless they protect it.” That’s the good thing. The idea here is China will need to worry about cyber-theft as well.
Also, since the Chinese economy is in distress, they are less likely to be a good global citizen.
China’s distress is good for the US – because they need access to the American market.
From there he went on to discuss the North Korea hacking of Sony Pictures because of the movie The Interview.
The hackers though were using Chinese IP addresses (Unit 121). He said this shows the Chinese government was complicit in this attack. Especially since all the data from Sony had to pass through the Great Chinese Firewall.
We know in 2012 North Korea and Iran signed an agreement to cooperate in cyberspace.
“Washington can not let others – especially Russia, North Korea, China and Iran decide what we read and have access to.” referring to the plot to stop us from seeing the movie. From there we went on to say this will continue until Washington stops if from happening.
Paul Syverson, the creator of Tor takes the stage.
He thinks the Dark Web will be a common way we access the internet for security reasons. He gave an example of his experience in the Navy – where they routinely tell people not to walk around with identifying clothing that connects you with the Pentagon, etc.
In other words, conceal your identity for safety reasons.
He then explained how a person in the hotel room – connecting to their home websites can be identified as working for the Navy, Apple, etc.
This is even worse from a security standpoint as they know where the person is sleeping.
He said a VPN would also be an issue – it is trackable as well. He said this is why the architecture is the way it is – using crypto and a circuit through the network allowing data to be passed between the server and user.
He said users and law enforcement benefit from Tor but criminals can still operate without Tor – they have many other tools.
He says the current web isn’t secure – routes can be hijacked allowing others to see where traffic is coming from and going to. DNSSEC protects only .15% of .com sites. Routes can be observed by BGP hijack and observation. TLS certificates are also subject to hijack and man in the middle attacks.
“The ordinary web is dark”
.onion addresses are self-authenticating so there is no chance for man in the middle attacks via certificates.
There is music and literary works as well as IM clients than live only as .Onion sites or Dark Web.
People can use .Onion sites to administer systems behind a firewall.
Ahmia is the search engine for the Dark Web – onion sites comprise about 5% of total Tor traffic.
He referred to Facebook having over a million Dark Web users.
He refereed once again to the .Onion way of accessing websites as being secure – as opposed to traditional web surfing.
Medical identity theft is a growing problem – medical sites are launching .Onion sites to prevent this. Likewise for government sites.
Onion sites are for stronger authentication – not just location hiding.
Brian Kontos of Securonix launches “Inside the Insider” presentation – he gave an elongated version of this presentation at the Pentagon last week.
There are numerous insider threat types. Yonggang Min at Dupont was able to steal 22,000 document from the company to share with a competitor. The breach cost the company $400 million!
He gave the example of American Superconductor – where China was able to get access to their source code thanks to a worker who shared secrets in China. The Chinese company then started to export products to the US. Check out the Great Brain Robbery for more (subscription required).
Millennials are hacking for ideological reasons – as opposed to money which was the traditional driver.
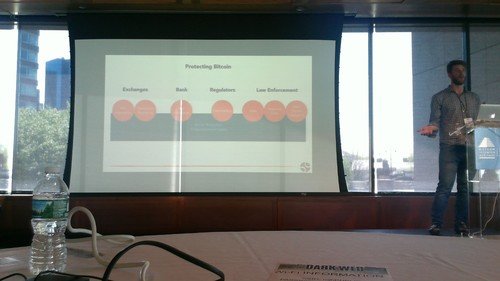
Jonathan Levin of Chainalysis takes the stage to discuss the Golden Strings of the Dark Web.
“The Dark Web is an economy like no other”
“Bitcoin is censorship-resistant and no one shuts it down.”
Discussion of ransomware (see related stories about Congress getting hit and the FBI warning).
He sees ransomware as the first thing being priced in bitcoin – not US dollars converted to bitcoins. This is the emergence of the bitcoin economy. There are call centers that let you negotiate and instruct you how to get bitcoin.
Ransomware hackers are now launching affiliate programs – allowing others to “resell” or “reinfect” computers to share in the profits.
A CNN Money reporter who wrote a book on Bitcoin asked if he could use his bitcoin tracking tool to track someone like Dread Pirate Roberts the founder of Silk Road. The answer was yes.
Alex Urbelis from Blackstone Law Group and an Information Security company Black Chambers started off discussing the debate between Apple and law enforcement – specifically, if the government can force manufacturers to defeat the security of their own devices.
There are state bills that say by 2017 companies can be fined $2,500 per device they cannot decrypt “without the necessity of obtaining the user passcode.” Examples were produced from Louisiana, New York and California.
The federal government is supporting this reach into devices and software as can be seen above.
Similar rules are being proposed in the UK.
Tech companies have complained saying this harms companies designing or developing products in the US and furthermore that these backdoors will b discovered.
Cloud data woul
d also be affected by government regulations – especially if data is cached or stored locally on devices in particular states.
There is no obligation by cloud vendors to tell customers that they have given data to the government.
In other words, your privacy rights are given up when they are stored in the cloud.
The was a question about the Rule 41 change that lets government get access to equipment that they might not otherwise have access to. He says it is good that senators are pushing back on this issue.
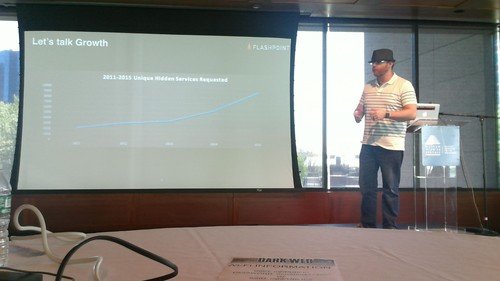
Lance James Chief Scientist at Flashpoint – former head of cyber intelligence at Deloitte & Touche takes the stage.
His company does research in the dark web space and has information to share.
Tor is growing when it comes to onion sites.There has been 24% growth in onions between 2014-2015.
Running your own hidden request directory gives you a good understanding of the dark web. They classify sites – he gave examples of different types of sites – age of site – newer ones with lots of traffic are suspicious.
One way of differentiating sites is to determine if it is a static page – if it is and gets a lot of traffic and has words like decrypt and files on it, it is likely ransomware.
Basically, his company is working on a solution to classify dark web sites into ransomware, commerce, etc.
Cybercriminals work in a chain of command structure like a company or the military. hackers share information and quite often hackers for hire will not go after targets in their own countries but instead go after targets beyond their borders so as not to raise scrutiny in their home areas. Forums allow criminals to share information and add on to services from one another.
China is two years behind Russia in cybercrime but they are using the techniques which have been successful in Russia and they are catching up. To get around censors, they use terms on forums which refer to hacking but are disguised as words which ore in the common language.
Hopefully that gives you a great taste of this unique educational experience. There was a great deal of amazing content above and beyond what has been shared here. To find out the event’s future dates, register and sponsor – please check out the website or reach out!