We are in Miami Florida – October 14, 2019, at the Fountainbleau Hotel where we are about to kick off. Here are some photos and tweets from last night.
8:30ish am:
CEO Serguei Beloussov about to take the stage.

Discusses his past – at Solomon Software which was sold to Microsoft.
Acronis is 16 years old as a seperate entity, 19 as a brand.
1,000 peopel registered – peopel here from 57 countries. Even the typhoon didn’t stop the Japanese from coming :-).

The world is becoming digital.

It is very different from the physical world.

Very difficult to protect the digital world – complexity, security, cost.
“The traditional security approach no longer works today,”

5 vectors of cybersecurity in the digital world.
Without complexity – with security, at a reasonable cost.
$250B market growing double-digits.
“We have the only solution -, especially with edge and endpoint.”
Single product with one UI, management integration, product and tech integration.

We spend a great deal on research and innovation.
We innovate with blockchain and AI.
There will always be people who can exploit software defects – and people will be people.

We keep a safe and secure copy of infrastructure and can recall it.
We can do proper forensics.

Nick “CyberNick” Grebennikoff takes the stage to discuss Acronis Cyber Protect.
Product discussion – single pane of glass management – continuous integrated protection, data classification and risk assessment, smart protection plans, safe endpoint recovery, forensics investigation-friendly.
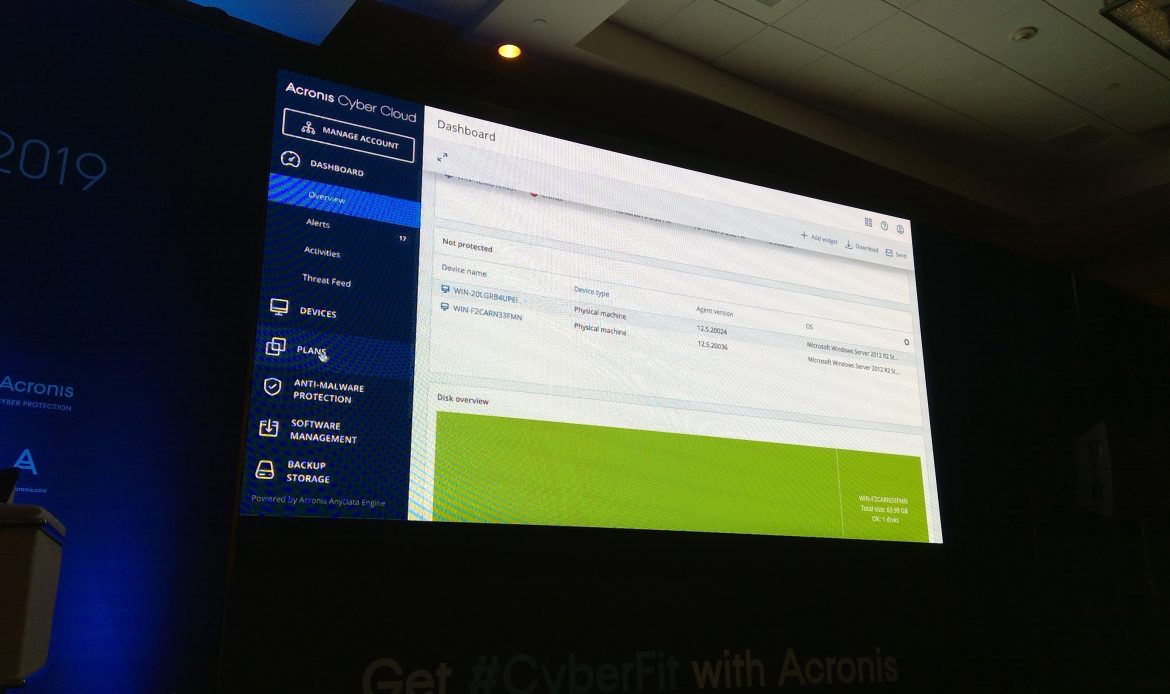
Shows sample of how it works.
Patch management – their team works behind the scenes to see which patches are good to be installed, etc.
Can detect which hard drives could potentially fail.
They scan the backups at night – don’t need to scan workstations.
They have a whitelist to prevent false positives.
9:12 am: Serguei comes back on stage.
You want proactive monitoring on who has access to your system.
Behavioral access control – we monitor user behavior and signal when something strange is happening.

The company also has “Cyber Infrastructure”
Cloud solution which seems to be a “secure and easy to use AWS-like service”

Secondary infrastructure – very secure.

9:21: Alex Miro takes stage to discuss Cyber Infrastructure.
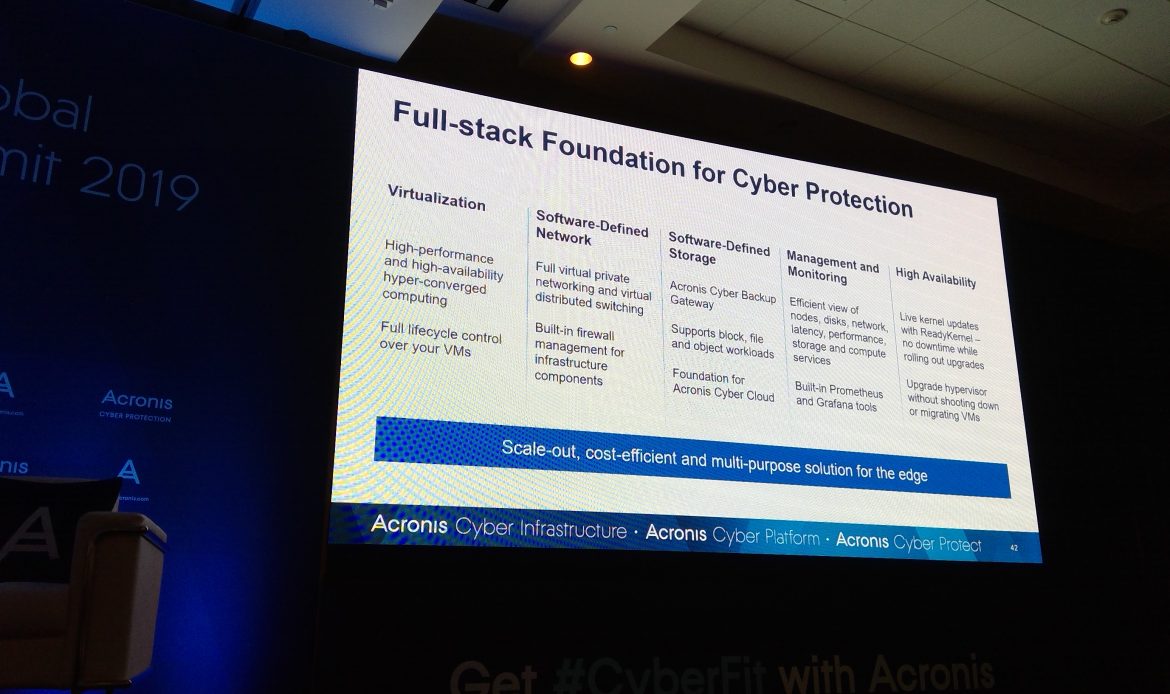
You can determine resilience against data loss based on customer, price point, etc. Can leverage existing hardware investments.
Have full control.
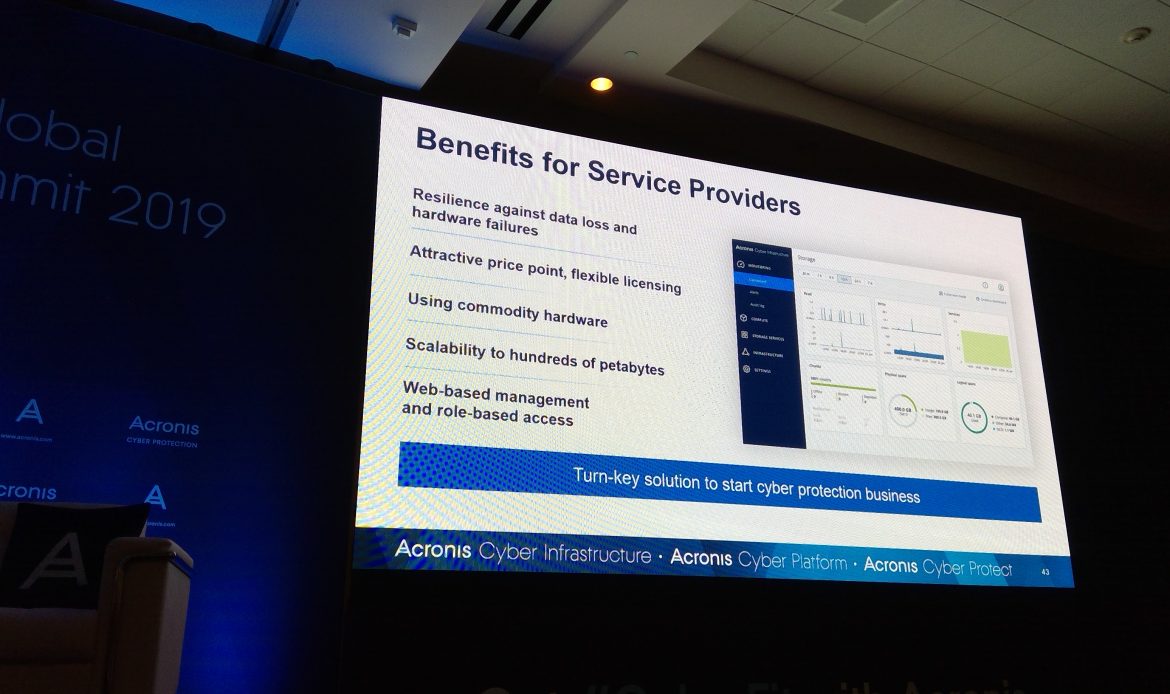
Or they can help with hardware.
Hundreds of zettabytes being managed currently.
Simple customer installation – then registration, management, backup config, DR config, protection status monitoring, restore and failover. Took us through how it works. Everything can be configured from the cloud.
9:33 am Stas Protassov takes the stage.

Acronis Cyber Platform – the core is SDKs. This allows partners and customers to extend the Acronis platform.

We are building a team of technical evangelists.
We have documentation with an API reference.
It also has samples and integration guides.
Use the most popular programming languages.
“It’s much harder for customers to leave you when they purchase multiple products from you,” Sergeui.

9:43 am James Abercrombie takes stage
You can meet your customer needs – not justy sell one product.

Multi-tier, multi-tennant, designed for MSP.
You can use white labeling to reinforce your unique brand.
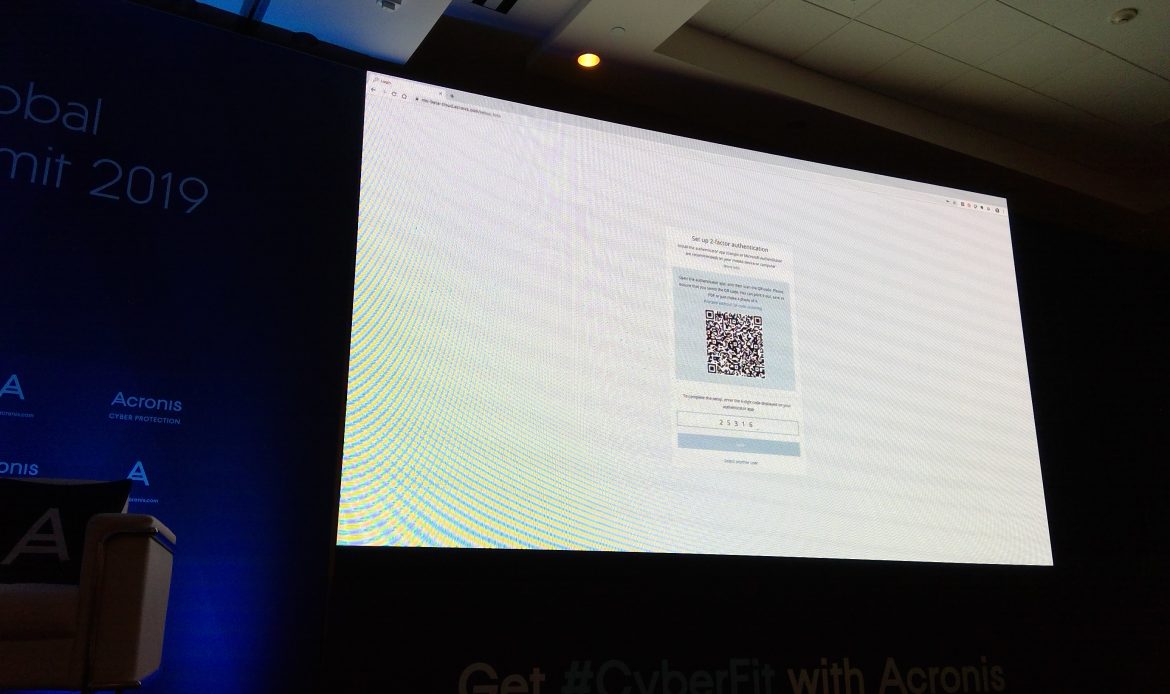
2FA demo. Turned it off and on to see how it works.
Discussion of backups – independent retention policies – backup in five different locations.
Can use group backup plans.
G Suit and O365 integration – people added and deleted automatically in backup without manual intervention.
DR functionality.
Can log into DR cloud – get access to the original system.
10:03 am Gaidar Magdanurov CMO

Use cases with sports teams.

Through sports – we can engage more people.

Francis X. Suarez Mayor of Miami takes stage to discuss the importance of cybersecurity.
10:30 am Robert Herjavec Cp-host of SharkTank and founder of Herjavec Group

Funny and engaging to start – a discussion of how cybersecurity has become mainstream.
SharkTank started as Golden Tiger in Japan, then Canada as Dragon’s Den.
Then Mark renamed it Shark Tank.
He ended up doing Dancing With The Stars because his mother said one day he would be on the show!
He started selling firewalls with Checkpoint. He ran the largest Cisco VAR in Canada at the time.
His company manages SOCs.
“Every year the world creates more data than the last 50 years before it!”
Cybersecurity went from being a carbon monoxide detector to smoke detector – showing people do things when they have to.
50% of security decisions coming as a result of regulations.
The average car being produced recently has three IP addresses. Dormant for now.
We are in the business of mitigating risk – not bits and bytes.
Change the conversation to a business conversation.

11:22 am Renee Bergeron SVP Global Channel Ingram Micro.
Discussion of recent attacks, fines, penalties paid.
Billion dollars or more in fines!
Discussion of partner MSPs who are growing via cloud.
Their CloudBlue has 1,000 different solutions.
“You don’t need to become an MSSP to take advatage of cybersecurity.”
11:53 am: Eric O’Neill Former FBI Counterterrorism and Counterintelligence Operative

Great discussion on history of cyberspies.
Hackers of today are using social engineering – there are no hackers, only spies.
Hacking is the evolution of espionage.
Ransomware: #1 way foreign intelligence attempting infrastructure attacks – banks, power, communications, etc.
We need to hunt the threat before the threat hunts us!
23% of Ransomware attacks using EternalBlue.
12:48 pm: Media Q&A with CEO Serguei Beloussov.
IDC: Will there conflicts in the channel as you extend your solutions?

Serguei: We give control – partners compete with each other and some of our offerings. He mentioned Intel and Microsoft which enable many customers – some compete with one another.
Question: Will people spend more or less on cybersecurity in ten years?
Serguei: People will spend more. The market is growing at 12% or so.
Question: Will AI and ML make lives easier.
Serguei: Both sides will it – but the good guys are in the open. The bad guys have the advantage. As long as there are humans involved… Its not going to stop.
Question: How will Goldman Sachs investment affect R&D?
Serguei: Not healthy for us to hire more than 20% a year globally.
He learned this from Apple – he alluded to the fact that there are so many quality people out there.
In three-five years, we want to grow five-ten times.
It’s a super-fragmented space.
We use 40 security tools at Acronis.
Harry Brelsford from SMB Nation asked about Sophos acquisition.
Serguei: Sophos is a good company – not popular in SMB space yet. Pure security solutions are no longer an option. Thoma Bravo owns ConnectWise and they are a partner.
That’s it for today – more to come tomorrow: Tues, October 15, 2019 (unless something really big happens).
Speaking of tomorrow – hear me speak – moderate at the following session:
Panel: ISVs and SPs
Retain More Customers with 3rd Party Services Integration
4:10 pm, Tues, October 15, 2019 in the Dazzle room.
10/15/2019 Tues: Dan Haven takes the stage.

Serguei comes back on stage.
Thanks the sponsors (a must for any event 🙂 )

Mentioned some of the platforms has team has built in the past.

Discussion of the platform – overview… The developers are the most important part.

He showed the famous Steve Ballmer “Developers” video.
You can make a difference by changing the customer offerings and it will reduce churn…

8:58 am: Stas Protassov takes the stage.
We want to protect all your data and provide full cyber protection.

We built this platform – by using these SDKs ourselves.

We need to give people a way to describe the data format – so our platform will understand and use it.
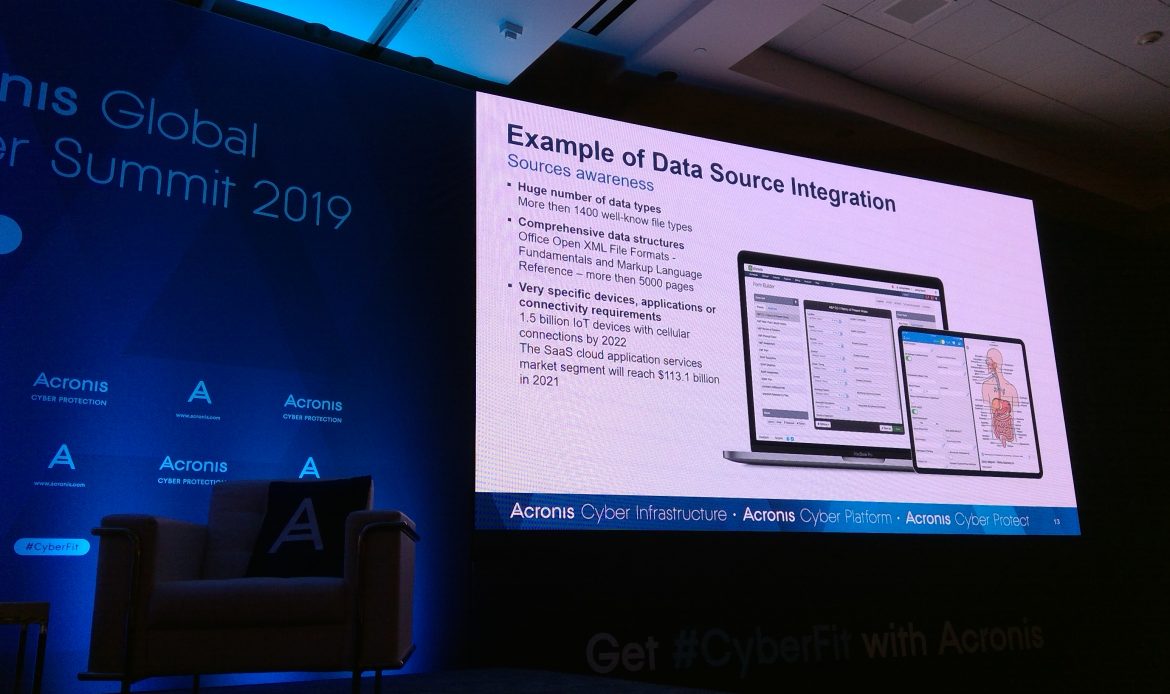
Here is an example of a medical platform using our platform to store the data. This is why we build a data source SDK.

Supported data destinations.
We developed Data Destination SDK to determine where the data should reside.
We have cross-product integration allowing our medical application – Files and Notary to transmit medical data from doctor to doctor.
9:09 am: Karen Elzari takes stage.
Security analyst and writer.


She was inspired by the movie Hackers with Angelina Jolie.
They were the good guys.
It was one of the first cases of Ransomware in history.

I am now a researcher in Tele Aviv University and others.
Discussion of WannaCry and its effect on medical devices – what if viruses of the future change the workings of MRI machines she surmised?
Moving on to Ransomware – impacting the trust people have in services.
Mention of FBI of PSA on Ransomware -we covered this here and here.
37% of Microsoft operating systems are running Windows 7 and they go end of support in three months.
Mention of Shodan.io – allows you to search for devices on the Internet which are not protected.
It allows you to do things like stop a cable car.
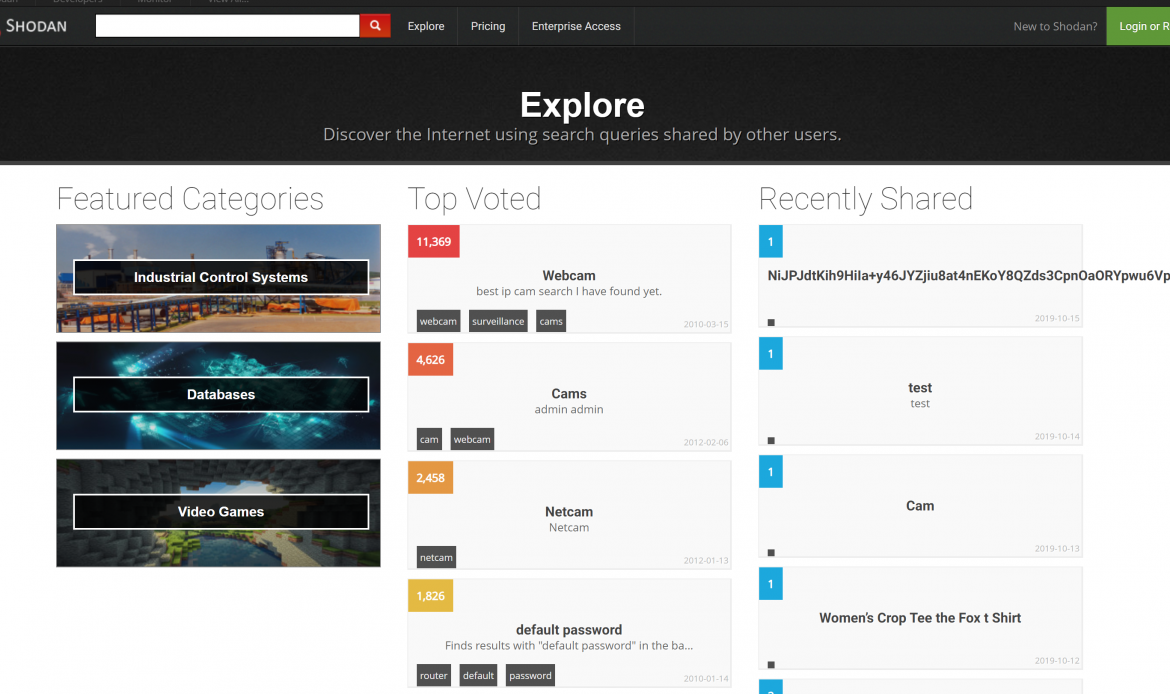
Discussion of cryptomining – Starbucks in Argentina, Pirate Bay, etc.
WannaCry ransomware has been redeveloped into WannaMine for Monero mining!
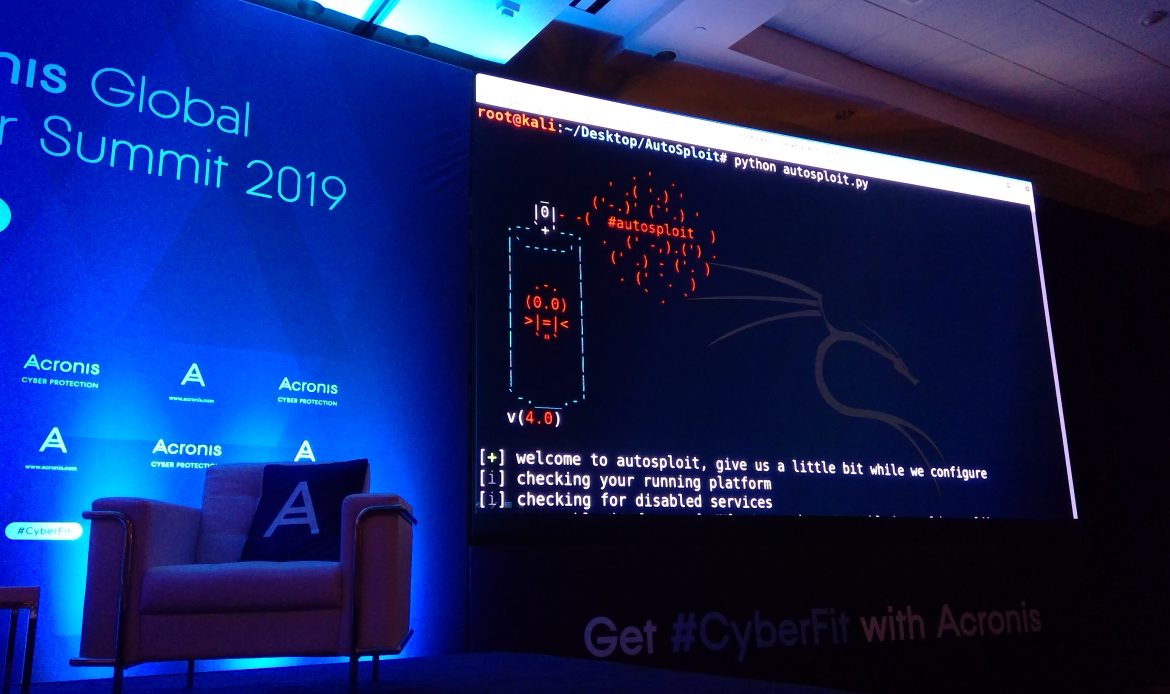
Shodan and Metasploit joined with 400 python lines – allows for the creation of Autosploit – you can launch exploits against vulnerabilities.
Version 4 is out already.
DeepFake voices are available – this means if you call a CEO to confirm a wire transfer you think is fraudulent – the CEO – you think you are speaking with might not be them.
Mention of Jack H. Cable – he was an ethical hacker that won a Tesla white hat challenge and now teaches at Stanford.
9:57: Ronan McCurtin Regional VP, Northern Europe.
Introduction of Michael Frisby, Managing Director with Vuzion.

Cloud provider – allows the selling of numerous customers.
We are moving to a MRR world.
Once you move customers to cloud – partners like Acronis keeps them current. We need to acquire as many customers as we can right now.
We have to continue to invest in people and education – to allocate time for people in the organization to learn.

Vuzion product line.
11: 00 am: Panel on Government Cybersecurity

You need to have all data available in government.
We need to know how much we can trust the output of AI and how much human control is needed.
How much autonomy can you delegate to a system?
The state needs to set up one organization with universities and private industry to work together.
GDPR: Causing dilemmas for multinational companies – which laws apply, where? Complying with standards like PCI, DSS, ISO helps.
The U.S. Federal Government does not have a good channel to distribute cybersecurity information to many government agencies. There should be federal guidelines or coordination which can be pushed down to agencies.
The Kurds in Iraq allowed no computers or cell phones in government offices to ensure cybersecurity – that’s a solution but it is not where we are going.
How do you give at the federal level the CISO the authority to respond and innovate?
You get pushed aside in government if you don’t follow the rules – if you try to be creative you don’t last.
We are breaking for lunch – that’s it for now.
12:11 pm: Recap:
This was the first Acronis event – we were honored to be asked to moderate the panel and be part of it. It seemed to go very well and the company is very ambitious – we expect really big things from them in the future.
—-
Make sure to join us in the session we are moderating today:
Panel: ISVs and SPs
Retain More Customers with 3rd Party Services Integration
4:10 pm, Tues, October 15, 2019 in the Dazzle room.






