In an effort to help protect our company and our customers’ from wcrypt, we documented in this post a series of steps followed by our incident response team which temporarily re-enforced our cyber defenses. To gain some background on this ransomware, the initial infection was stopped by a researcher that stumbled across the kill switch and ended up saving a lot of people. However, this measure was only a stopgap as the malware author(s) or another person could easily repackage this contagion with a craftier sandbox test mechanism.
Beyond making sure that all Windows systems have been patched against the MS17-010 exploit, we decided to take the unusual step of blocking all switch (Cisco 3850) ports from communicating using SMB (port 445) inbound. This was done everywhere except on a handful of servers until we were able to ensure that our systems were not vulnerable.
Sales 3850 stack ACL:
- ip access-list extended no-smb-host2host
- permit tcp any host 10.1.5.1 eq 445
- permit tcp any host 10.1.4.235 eq 445
- permit tcp any host 10.1.5.2 eq 445
- deny tcp any any eq 445
- permit ip any any
We applied an ACL to all user ports inbound and outbound on the uplink.
Core 3850 stack:
- ip access-list extended no-smb-host2host
- 10 permit tcp any host 10.1.5.1 eq 445
- 20 permit tcp any host 10.1.4.235 eq 445
- 30 permit tcp any host 10.1.5.2 eq 445
- 40 permit tcp any host 10.1.15.158 eq 445
- 50 deny tcp any any eq 445
- 60 permit ip any any
An ACL was also applied to all Gig ports, ten gig uplinks and our wireless networks.
We also disabled SMB1 on the domain controllers and the servers that hosted critical applications such as our accounting application using Microsoft’s recommended commands. While these changes didn’t protect remote users, it did protect the rest of the network. There were of course repercussions from this change in the ACLs.
As a result of these changes, end users weren’t able to share files directly between PCs. To do this they had to use our file shares or another secure protocol. Again, this was only a temporary change until we were absolutely sure that all our systems were properly patched. Only then were the ACLs removed.
To verify that SMB communication had been contained by the temporary ACLs, we use Scrutinizer as a network traffic analytics system to find all SMB traffic. If we found traffic where it shouldn’t be, we addressed the issue.
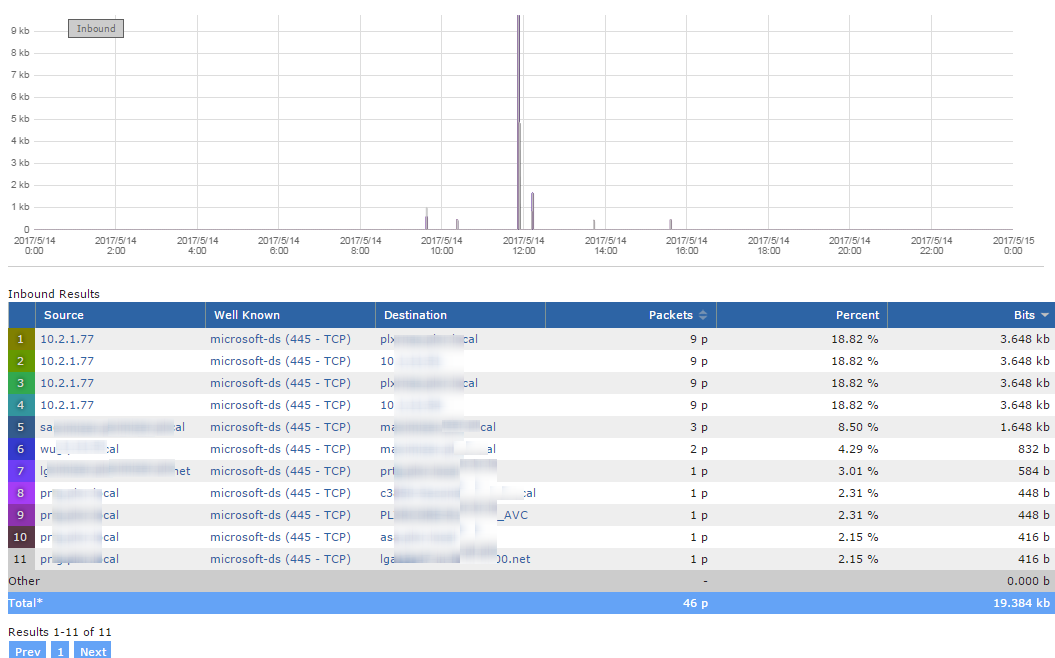
As a result of these changes, if some device had connected with an infected machine they wouldn't have been able to connect to any of our resources. This meant that they couldn’t infect others or propagate the malware on these ports.
If you need help understanding this post or need assistance setting up this type of configuration, reach out to the team at plixer.









Leave a comment