| Ratings | Score |
| Installation | |
| Documentation | |
| Features | |
| Usability | |
| Performance | |
| Overall |
Well... Pop quiz, hotshot. Your web server goes down on a weekend. Once the web server loses 50,000 page views, you lose $2000 in ad revenue. If it drops below 50,000 pageviews you "Mr. IT Administrator" will lose your job. What do you do? What do you do?
Putting aside the Speed movie reference for a moment (couldn't resist
Ah, but you can.. you can... Using Dataprobe's series of iBootBar products, you can remotely recycle power simply using a Web browser interface or for the techies you can even telnet into the iBootBar and issue various commands. It also sports an internal modem with both data and DTMF tone dial control. Some of their models include a modem (i.e. iBB-2N15-M) so you can even dial-in via the the telephone with guided voice prompts and status information or remotely connect using a modem terminal program. TMC Labs was sent an iBootBar to test and so I was lucky enough to play around with this potential weekend & career lifesaver.
I hooked up their iBB-2N15 (2 x NEMA 30 Amp) model (list price $500) which includes 8 outlets segmented into 2 separate power outlets (A & B ) each with their own power cord. The beauty of this segmented setup is realized when you are connecting servers with dual-redundant power supplies. You can group the two outlets together and reboot them in combination or if for whatever reason you need to change the outlet connection, such as when installing a new UPS, you can gracefully bring one outlet down while the other still stays up since it's connected to a separate power outlet.


North American version - 15 or 20 Amps, Single or Dual Power Inlets

International version - 10 or 20 Amps, Single or Dual Power Inlets
Next, I had to configure the IP address which defaults to 192.168.0.254. I used telnet to change the IP address and gateway settings to match our LAN configuration. I also changed the default username and password. Then I launched a browser, typed in the IP address, and logged in.
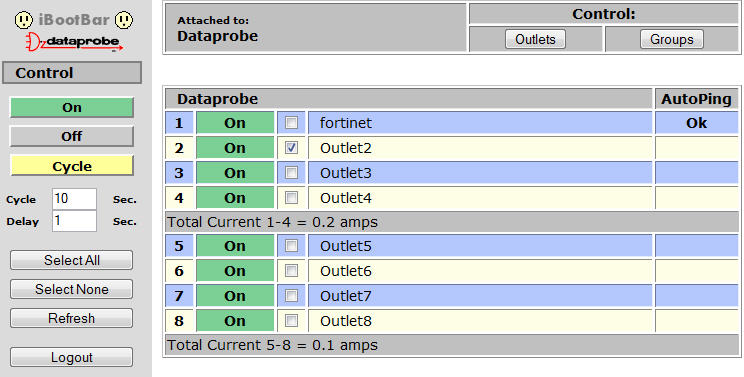
From the web interface you can simply select a single outlet, multiple outlets, or an outlet group and then perform an action, which includes: turn outlet(s) on, off, or cycle (off/on). Pretty straightforward. The web interface hides most of the advanced functionality, which must be done via telnet. That's probably my main usability complaint is the fact that you have to use telnet to do all your configurations, but I suppose that adds a layer of security.
The telnet interface accessible via a serial cable (RS232) or via IP address. You can add additional users and assign permission for that user to a specific outlet or group, allowing different IT staff to only have access to specific servers that they are responsible for. The telnet interface is pretty easy to use and includes several commands, including:
set outlet <n> <on/off/cycle>
set outlet <n> name <name>
get outlet <n> initial.state
set outlet <n> initial.state <last/on/off>
get outlet <n> autoping
set outlet <n> autoping ipaddress <dotted decimal>
set outlet <n> autoping action <action>
action = none/on-latch/on-follow/off-latch/off-follow/cycle/cycle-once
set outlet <n> autoping frequency <0..999>
set outlet <n> autoping count <0.99>
The most interesting of the commands is autoping, which will actually PING the server/device's IP address that you assigned to a specific outlet. After a certain number of pings has failed (autoping count) you can have the iBootBar cycle the power to the outlet. I configured it to autoping our firewall's internal IP address and recycle the power to Outlet1 after 20 failed ping attempts. It will only cycle the power once and won’t recycle again until the ping is restored. This prevents the iBootBar from constantly killing the power if for example I am reconfiguring something on our network that knocks the firewall off the network. You can also set it to constantly recycle the power, but you just have to be careful to set the "autoping count" setting fairly high to give enough time for your device to reboot and reach a "pingable" state.
The beauty of the autoping feature is you can set it and forget it. It can be 4am and if the device fails, the iBootBar will automatically recycle power to the device. No need to respond to a 4am beeper/page and manually do this. Ah, the beauty of technology! Pretty soon we won't even need IT folk! I'm kidding. If anything, IT admins will be in more demand as technology becomes increasingly complex and requires more integration with other systems.
In any event, I should mention that the iBootBar supports SNMP alerts as well as email alerts that leverage SMTP. It also supports SSL (HTTPS) for additional security. And speaking of security, a co-worker, Vahid Hashemian and I discovered that you can easily hack into the iBootBar. The iBootBar uses a static cookie defined as DCRABBIT="0". Simply creating this cookie on my PC allowed me to bypass the username/password screen and get right in. Thus, in theory, I can access any iBootBar where I knew the IP address.
 Hacking the U.S. Senate...
Hacking the U.S. Senate...Ironically, I was sent a case study where the U.S. Senate uses the Dataprobe iBootBar to monitor the audio network devices in all of the remote hearing rooms. So in theory, I could have remotely recycled the power to the microphones during the General Petraeus hearings to cut out ridiculous accusatory statements like “I think that the reports that you [Gen. Petraeus] provide to us really require the willing suspension of disbelief" Come to think of it, didn't General Petraeus's microphone not work at the beginning of his testimony? I plead the 5th!
Joking aside, I love the iBootBar. I wouldn't map the internal IP address to an outside IP address until they offer a firmware fix for the cookie security issue - I'd just stick with telnet, but all-in-all, this device is indeed a lifesaver and a worthy asset to any IT/network administrator's arsenal.
Pricing as tested: $500. ($650 for the optional modem modem)
Update: I just spoke with Dataprobe and they told me they fixed the problem in a beta version of the firmware that is yet to be released. They sent me the beta firmware, but when I tested it it didn't seem to fix the cookie security issue. I was able to send a POST command (cycle=&delay=&mainAction+6+=1&mainCommand=1) using DCCOOKIE="1" using a browser simulator tool and was able to cycle power to the outlets without a username & password. I will have to follow-up with them tomorrow to let them know the beta doesn't fix the problem.
I should mention that the new beta also adds more functionality, including allowing a Windows program they are developing to connect to the iBootBar so you can configure it more easily than using a telnet session.