I reviewed CertainSafe for TMC Labs to be published in TMC's Internet Telephony Magazine. Check out an early sneak peek here...
TMC Labs learned about a new product launching by TransCertain called CertainSafe that could be a game changer when it comes to cloud-based collaboration. Fortune 1000 companies and indeed even smaller companies are reluctant to put their most sensitive and confidential data in the cloud to be shared with their partners and customers. But what if you could encrypt the data in the cloud using AES256 encryption or any encryption algorithm of your choice, and combine that with “Tokenization”? Further, what if you could share certain folders and files with specific people using just a browser and with no plugins required and what if you could set an expiration date of how long a folder is shared and maintain an extensive audit trail?
TMC Labs spoke with TransCertain’s CIO David Schoenberger about CertainSafe, along with their current product CertainStore, which is the engine that drives the security behind CertainSafe. David started by giving a history on TransCertain along with a technical description of CertainStore…
David: Four years ago, when we founded this company, my partner Tim Reynolds and I both came out of payment processing background and we worked with a couple of payment processors before. We had built some remarkable payment processing technology - highly secure processing and working directly with the Federal Reserve system and to the backbone of VISA and MasterCard. Direct high speed volume processing. We had to have high speed, high security, and high availability. Those were our three foundational hallmarks for the technology we built.
While we were in this payment processing business, our clients kept coming to us and saying hey, great, we understand you have fantastic security, you’ve got great speeds, but we’re also concerned about some other pieces of our data. What do you guys do for social security numbers or what about this documents that go along with the payment transaction? Can you secure that stuff too? And we couldn’t. The growing concern in the marketplace was that we’re not just concerned about payment data. In fact we might be more concerned about these other pieces of data than we are around the payment data.
So that’s what we did. Tim Reynolds and I left the company we were with and founded TransCertain with the idea that we can take any data from any platform and secure it. But not just secure it make it available. This availability is very revolutionary for us. We’ve bridged the gap between data security and data integration and availability and we have created a technology that secures data at very high speeds and very securely and at the same time makes it available.
Unlike bulk database encryption solutions which encrypt everything, CertainStore helps companies identify which items in their database would give the company heartburn if there was a breach. What CertainStore does is take those elements from their database and provide the customer a “token” just as a reference or placeholder. They take the secret data and put it in CertainStore’s cloud through a proprietary algorithm to generate the token, which importantly has nothing to do with the source data. So if someone hacks in and finds those millions of tokens sitting in the client’s database, they won’t be able to reverse engineer the originating data.
TMC Labs: What about a rogue employee that attempts to contact TransCertain with all of the tokens and asks for the data back?
David explained that programmatically, even if they contact TransCertain, they cannot give the data back unless the permissions have been granted in the business negotiations to say what needs to happen to the data.
David: Typically, when we have the data, we’re doing something with the stored data. We can hand it to a vendor, to a bank, to the other doctor, the other insurance company. Typically speaking, we never hand the data back to the merchant. When they tell us to do something with the data they’ll hand us the token with the rule that’s already built into our platform called process on time that says ‘here’s what needs to happen to the data when it needs to happen. So if a hacker says hand the data back to me, our system will deny it.
TMC commented how this essentially eliminated “social engineering hacking” and David agreed that due to their “one way streets” or “one way rules”, it’s impossible to gain access to the data even if the tokens are acquired by a hacker or rogue employee. CertainStore spreads the data around to multiple hard drives in separate physical locations.
David: Even if the hacker figured everything out and broke through all the rules and understood every nuance of our technology, which I’m telling you this is impossible- and he took the token and hacked in and unencrypted this data represented by the Token and the hacker has found in the thousands of different hard drives where that piece of data lives, MicroEncrypted™ on that hard drive and took the data out. The best thing - which is still impossible – that they can ever do and if they are able to hack through the encryption algorithm, which standard ships with AES256, instead of unlocking an entire encrypted database, they’ll only be able to unlock one single element of that data.
He added that they can use whatever encryption algorithm a client wishes, including proprietary encryption algorithms.
TransAct is the final step, an adapter system they’ve built that unencrypts, transforms the data into a format the receiving side is expecting and then a Just in Time (JIT) sort of method, for the first time it unencrypt the data using the token and use the receiving side’s proprietary method of transmitting that data to them. The receiving side can use standards such as SSL for the transmitting of the data.
David mentioned that their solution completely relieves their clients of the burden of securing the data, any fines or penalties or media embarrassment if a client’s systems were hacked since no sensitive data was stolen. Their platform gives them complete control and freedom over what happens to that data and because CertainStore does not ever hand back that data to the client it eliminates the liability of “holding” that secret data locally. CertainStore acts as the go-between pushing the data where the client needs it to go without the client ever having to store sensitive data in their own IT infrastructure.
If the client wants the data back, CertainStore will give it back to them. In fact, there are cases where fields need to be updated or compared. CertainStore offers APIs to expose the data and allow the client to update records and re-encrypt and re-tokenize that data without clients having to do anything on the front-end.
CertainStore leverages Server-to-Server communication using standard Web Services so that their database communicates with TransCertain’s servers to provide the field-level encryption and what TransCertain calls “MicroTokenization”. These connections are completed utilizing technology that can connect any platform to any other platform quickly, efficiently, and cost effective.
David: All of our services – CertainStore, Process on Time, and TransAct are all wrapped with APIs, both XML and JSON APIs so any organization regardless of their front-end platform or regardless of their database can send and receive tokens from us, can send and receive the data that they need, can make the requests that they need programmatically at the server level. Which means from an integration standpoint the integration is a piece of cake. They don’t have to change their front-end software, or change their database, or change their legacy system, etc. All they have to do is make an XML or JSON call into our platform.
With a background on TransCertain and CertainStore complete, David proceeded to give a demonstration of CertainSafe, a Security-as-a-Service solution. TMC Labs was also granted a trial account to test it ourselves. CertainSafe is a web-based front-end built by TransCertain designed to be completely browser-based with no installation, leveraging HTML5, and built on TransCertain’s core foundation, of which CertainStore that we discussed previously is a core component. While CertainStore was designed for server-to-server communication with no human interaction, TransCertain built CertainSafe to be human-to-server communications.
What does CertainSafe do? Essentially, you can think of it as similar to a Dropbox or Box, but with an added layer of security and compliance – and when we say compliance we’re talking PCI DSS Level 1, plus AES256-level encryption, with support up to 1024-bit or any other custom algorithm that may be required. CertainSafe enables organizations to share mission critical information across multiple platforms at a high level of security you just don’t see unless you work for a government entity.
The popularity of Dropbox is due to its ability to easily share photos and documents with others as well as hosted backup. David explained, “We designed CertainSafe very specifically to say “we don’t want the bulk” We’re not the neighborhood storage unit. We’re in essence the virtual safety deposit box. This is for your files where you need compliancy and or high levels of security. You want stuff to have PCI-certified rubberstamp on it or you want to pull in your X-ray files. We don’t envision people using our service just for backup or storing vacation photos. This is for the real secret, sensitive stuff.”
When we first logged into CertainSafe as a new users we were prompted to pick out own security questions and then we could set how often after we login that we’re challenged. You can choose how often to be challenged, i.e. once per week, once a month, randomly, etc. Here’s an example: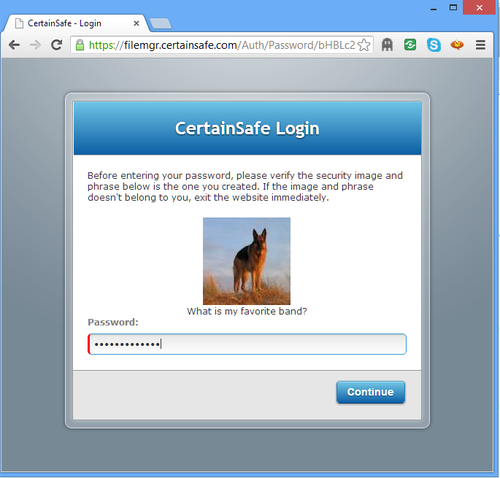
In CertainSafe you can create folders and then share the folder with other people, including people who are not currently CertainSafe users. Any CertainSafe user can share their folders and files with anyone, with the only caveat being that non-CertainSafe users only have “read” access and not “write / edit” access. The main folder and file management UI looks like this: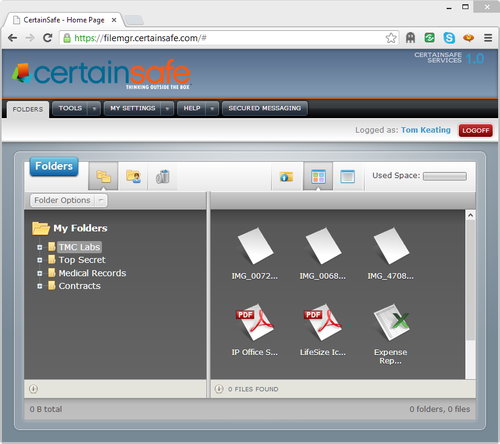
CertainSafe stores files in two different formats – the original file format and converted preview view if it’s a viewable item, such as an Excel, Word, PDF, or other format CertainSafe supports. It’s a non-editable secure view of the file and cannot be downloaded or printed. Though technically you could take a screenshot and print that. The system can store financial data or other confidential data because as previously mentioned, it is PCI DSS Level 1 certified with third-party auditing of this compliance.
Dragging and dropping files from your file manager (i.e. Windows Explorer, Apple Finder) into CertainSafe is a snap. In fact, you can drop-and-drop multiple files at once and through the magic of HTML5 you don’t even need a browser plugin to upload your files. Here’s a screenshot of the browser where you would simply drag-and-drop your files: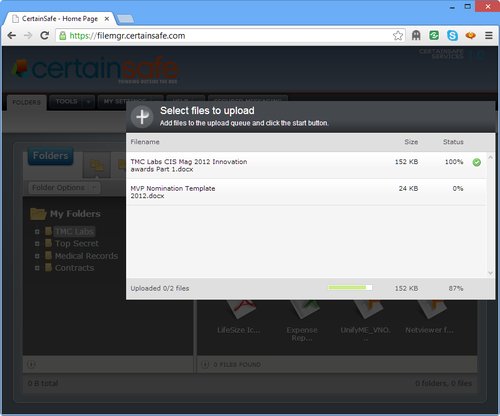
What happens on the back-end is the file is MicroEncrypted and has a token created. It is then stored in multiple locations, an converted into a viewable only document. It’s actually stored twice times four, because they have a data center in Denver (primary) and Salt Lake (hot site) with each data center having a 2nd redundant database. If any disaster happens it’s already running simultaneously at the hot site and essentially backed up an additional two times.
Importantly, when you share a folder you can set a data range, including the ability to share a folder in the future. Unlike Dropbox and other cloud-based sharing apps which require you to remember to “unshare” a folder at a later data, CertainSafe lets you set a sharing expiration data. This is important for reporting, HIPAA compliance, and other compliancy issues. Other sharing options allow you to set whether users can download the file, view the “preview” rendered document only, and even enable users to upload back into this folder. When viewing files you can view in icon view or in list view which lets you sort by date. A couple other handy file management capabilities include auto email notifications upon changes and auto email notifications for new items added.
TMC Labs mentioned how fax is considered a strong legal document because there is no stops in the middle unlike email which travels across multiple hops, can be spoofed, etc. and asked David was sort of legal standing CertainSafe has. David responded, “It’s similar to fax in that regard. This means that if you upload something it’s NOT going anyplace except into this compliant, certified, cloud-based application.”
Audit logs built into the system add further legal standing and enable clients to track who changed what and when. You can see when someone looked at a file, when it was looked at, and more. The web interface doesn’t display every bit of detail. For instance, CertainSafe tracks how long each user has been signed into a session but doesn’t display that information by default. CertainSafe records just about everything imaginable into their database and TransCertain can customize what audit information is displayed for their clients.
One useful feature is that users can attach comments to a document. This is useful for example for signing contacts – simply upload the contract and request the other person sign it with a comment. TransCertain told TMC Labs they are working on a digital signature feature for a more formalized signature process. Another useful feature for the enterprise is that administrators can set roles and permissions for users.
Secure Shred Option
When a file is deleted it is truly “shredded”. It is overwritten by binary data at minimum seven times. Forensically, four is enough to make the file unrecoverable, but TransCertain mentioned that the Department of Defense requires a minimum of seven times.
TransCertain demonstrated how an X-Ray can be shared in the cloud without delivering the X-ray to the doctor’s hard drive. This is not only important for HIPAA compliance, but it also solves the bandwidth issue of waiting for a 2GB file or larger to download. The X-ray image can be viewed from your browser with the image residing securely in the CertainSafe cloud.
Pricing:
Basic Individual - $9.99/mo each
Professional - $7.99/mo each
Enterprise - varies
|
Conclusion
TMC Labs inquired about future features in CertainSafe and they told us that Secure Chat is something in their R&D stage. We also asked about WebRTC (VoIP, Video) and they said that’s something they’re looking at as well.
Sharing and security are like matter and anti-matter – if they get close they destroy each other. How can you have high-level security and at the same time share the information without killing usability and making users jump through hoops to gain access? CertainSafe takes this sharing/security/usability paradox and turns it on its head, making information secure, PCI & HIPAA compliant, and very usable/user-friendly for the end-user. TMC Labs was very impressed with CertainSafe and would not hesitate to recommend their solution to organizations looking for a highly secure method of sharing information with high usability and at a cost that doesn’t break the bank.