 Those same rascals that figured out how to do call jacking on the popular BT Home Hub to make free "hacked" VoIP calls have done it again! GNUCitizen.org is a group of security experts that just discovered a vulnerability in the administrative web interface in snom Technology's model 320 VoIP phone. They way it was discovered is that a router hacking challenge was launched and which as a "side result" caused GNUCitizen to discover a security flaw in the snom 320 VoIP phone. In GNUCitizen's blow-by-blow discovery he writes, "Although not directly related to the router hacking contest, the results I’ve got were rather disturbing and made me get a totally new view on the VoIP phone security landscape." (I'll say...)
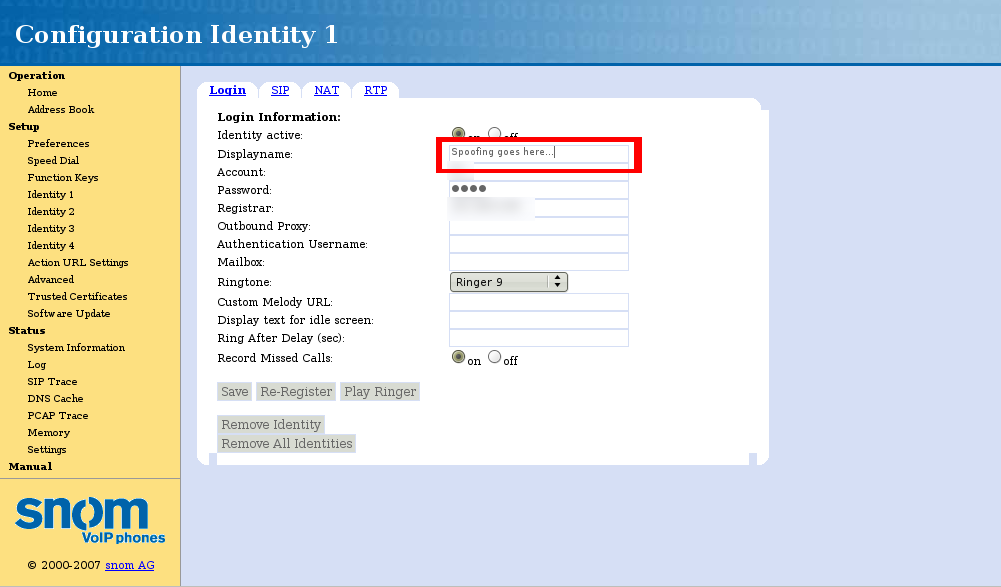
Those same rascals that figured out how to do call jacking on the popular BT Home Hub to make free "hacked" VoIP calls have done it again! GNUCitizen.org is a group of security experts that just discovered a vulnerability in the administrative web interface in snom Technology's model 320 VoIP phone. They way it was discovered is that a router hacking challenge was launched and which as a "side result" caused GNUCitizen to discover a security flaw in the snom 320 VoIP phone. In GNUCitizen's blow-by-blow discovery he writes, "Although not directly related to the router hacking contest, the results I’ve got were rather disturbing and made me get a totally new view on the VoIP phone security landscape." (I'll say...)The big hack involves the ability of some VoIP phones to make phone calls from the Web interface using a simple web POST request. The Snom 32x supports this feature which along with some security vulnerabilities is what GNUCitizen exploited to have some real fun, like ya know, making an outbound call using a spoofed CallerID. ![]() (see screenshot above. Click for large image.)
(see screenshot above. Click for large image.)
The website explains, "The Web interface of the Snom 32x VoIP phone suffers from many vulnerabilities that may cause financial and reputation trouble for the organizations that trusts them in their network. The vulnerabilities are based on common attack vectors, such as XSS and CSRF."
Hackers will need the IP address of the phone being targeted to launch the attack, but using a simple scanner they can use a cross-site scripting attack to hack the phone’s built-in management interface.
Fun Illegal stuff you can do:
Hackers will need the IP address of the phone being targeted to launch the attack, but using a simple scanner they can use a cross-site scripting attack to hack the phone’s built-in management interface.
- Steal the phone history from the logs including any other details attached to the calls via XHR.
- Poison the address book with a persistent XSS - the name is encoded correctly but not the phone number.
- Inject a JavaScript worm to gain total control over the user by changing the visible output by performing XHR-CSRF attack.
- Change the settings of registered phones, including the displayed text on the phone’s display.
Let’s have a look at a proper scenario. If the attacker knows the IP of the device’s Web interface he/she can disable and/or hijack the whole phone within a few minutes. By crafting a XSS-CSRF vector he/she can inject a persistent XSS into the address book. When the victim visits the phone book, the XSS worm is silently executed and the attacker gains a total control over the interface and the actions that will be performed in the future. This also circumvents any protection mechanisms like VPN or comparable network layers, etc. And yes, in the worst case scenario the attacker will be able to survey the sound in the room in and cleanup the logs afterwords.
GNUCitizen has posted proof-of-concept code and notified Snom about the vulnerability, however, snom had not yet responded as to when a new firmware patch might be available. VoIP security never seems to be at the top of anyone's "to do" list, but this news about a popular VoIP phone being hacked should open the eyes of CTOs, CIOs, and MIS managers looking to deploy VoIP phones, as well as the eyes of VoIP phone manufacturers such as snom, Aastra, Cisco, Polycom, Avaya, Nortel, etc. It'll be interesting to see how quickly snom patches their firmware. Stay tuned...