Employees using Corporate Bandwidth with Personal Phones
This big increase brings with it big concerns when it comes to network monitoring:
- How much bandwidth are all these additional devices collectively using and is it impacting business critical applications?
- What applications and web sites are users hitting and what impact are these distractions having on productivity and how often?
- What are the security implications introduced by allowing these devices onto the net? Many of these hand held devices do not have antivirus software.
Given that the traffic from a cell phone browsing a web site looks nearly identical to that of a PC hitting the same site, how can a company determine the amount of Internet bandwidth utilized by the combined smart phone devices? To answer this, we need a new flow element.
All hardware accessing the LAN utilizes a six byte hexadecimal MAC address. The first three bytes of this address is reserved to identify the vendor. For example, an iPhone may have an address of E4:CE:8F:C2:9D:AA. The first three bytes E4:CE:8F identifies the vendor ‘Apple’ and it is likely that thousands of other iPhones start with the same 3 bytes. The remaining three bytes C2:9D:AA are unique to the individual iPhone.
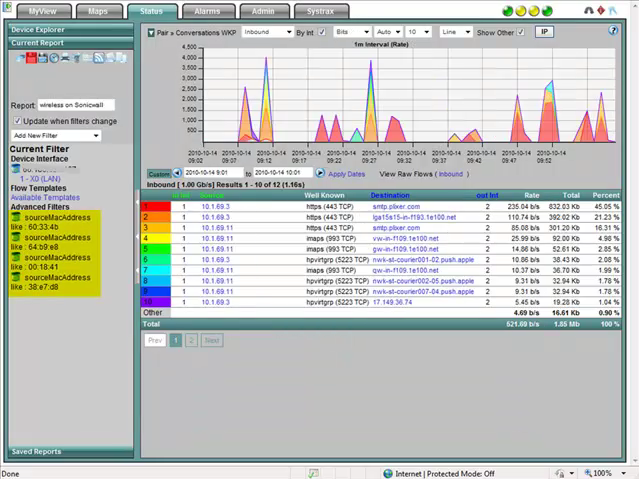
Nearly a dozen vendors (e.g. Cisco, Enterasys, Exinda, Juniper, nBox, Sonicwall) are now exporting MAC information in their flow exports. Learn how to export [MAC address with Flexible NetFlow] http://www.plixer.com/blog/netflow/getting-mac-addresses-from-netflow-v9/ . Setting up a simple network monitor will help you proactively keep track of this traffic.
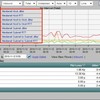
Below is an example of our partnership reporting with Enterasys NetFlow and mIAM exports:
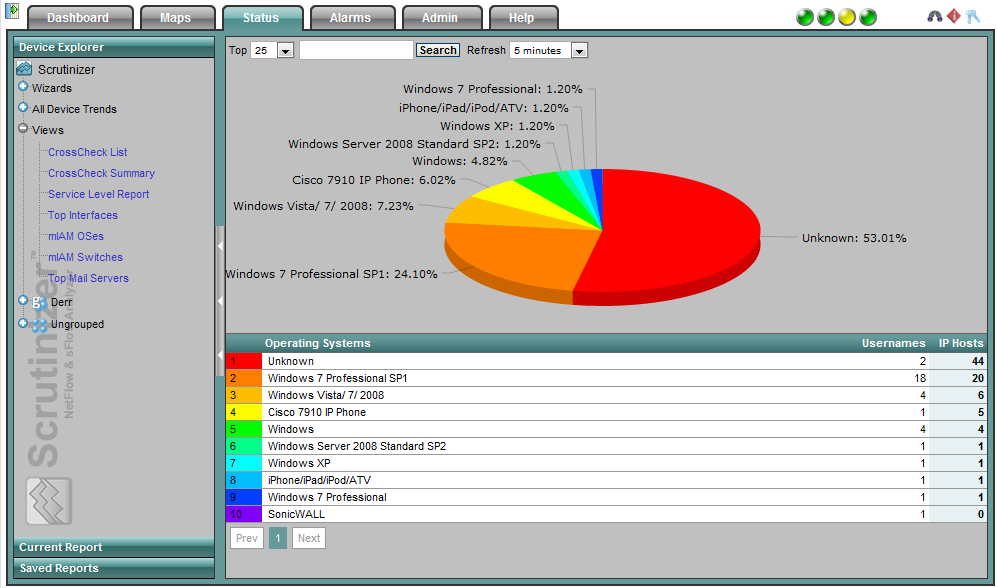
If your NetFlow or IPFIX hardware can export Username, you could click on a username and see the number of devices authenticated by the same user.
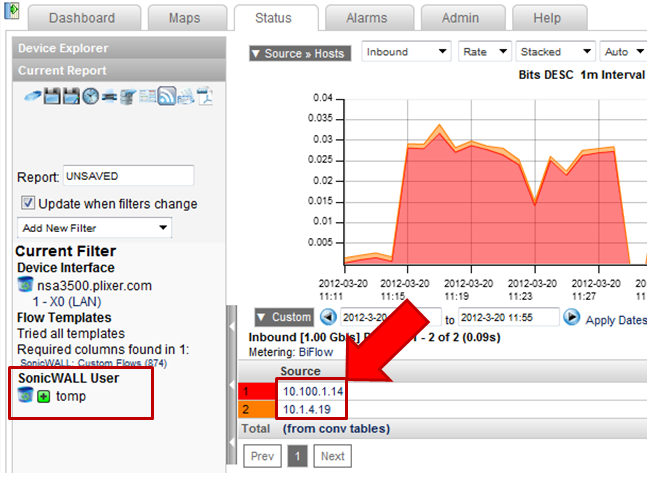
Monitoring BYOD traffic is a growing concern and the above report can be run against flow exports from the Cisco ASA, Palo Alto Networks and the SonicWALL (example above). Vendors are always looking for new and innovative ways to filter on this data.
[Gartner predicts that 645 million smartphones] http://www.channelinsider.com/c/a/Mobile-Devices/Mobile-Management-Styles-Driven-by-Consumerization-Gartner-634465/ will be sold in 2012 – a 40% increase from this year. Cell phone reception is often weak on the interior of office buildings and smartphone owners will have their WiFi on. Many companies are allowing employees onto the corporate net with their personal smart phones in hopes of increased productivity.
Employees using Corporate Bandwidth with Personal Phones
This big increase brings with it big concerns when it comes to network monitoring:
1. How much bandwidth are all these additional devices collectively using and is it impacting business critical applications?
2. What applications and web sites are users hitting and what impact are these distractions having on productivity and how often?
3. What are the security implications introduced by allowing these devices onto the net? Many of these hand held devices do not have antivirus software.
Given that the traffic from a cell phone browsing a web site looks nearly identical to that of a PC hitting the same site, how can a company determine the amount of Internet bandwidth utilized by the combined smart phone devices? To answer this, we need a new flow element.
All hardware accessing the LAN utilizes a six byte hexadecimal MAC address. The first three bytes of this address is reserved to identify the vendor. For example, an iPhone may have an address of E4:CE:8F:C2:9D:AA. The first three bytes E4:CE:8F identifies the vendor ‘Apple’ and it is likely that thousands of other iPhones start with the same 3 bytes. The remaining three bytes C2:9D:AA are unique to the individual iPhone.
<<< monitoringMobilePhoneTraffic.png >>>
Nearly a dozen vendors (e.g. Cisco, Enterasys, Exinda, Juniper, nBox, Sonicwall) are now exporting MAC information in their flow exports. Learn how to export [MAC address with Flexible NetFlow] http://www.plixer.com/blog/netflow/getting-mac-addresses-from-netflow-v9/ . Setting up a simple network monitor will help you proactively keep track of this traffic.
If your NetFlow or IPFIX hardware can export Username, you could click on a username and see the number of devices authenticated by the same user.
<<< sonicwall-Ipfix-username.png >>>
Monitoring BYOD traffic is a growing concern and the above report can be run against flow exports from the Cisco ASA, Palo Alto Networks and the SonicWALL (example above). Vendors are always looking for new and innovative ways to filter on this data.
KEY WORDS:
network monitoring
flexible netflow
network monitor
monitoring mobile phone traffic
monitoring byod traffic
big concerns when it comes to network monitoring:
1. How much bandwidth are all these additional devices collectively using and is it impacting business critical applications?
2. What applications and web sites are users hitting and what impact are these distractions having on productivity and how often?
3. What are the security implications introduced by allowing these devices onto the net? Many of these hand held devices do not have antivirus software.
Given that the traffic from a cell phone browsing a web site looks nearly identical to that of a PC hitting the same site, how can a company determine the amount of Internet bandwidth utilized by the combined smart phone devices? To answer this, we need a new flow element.
All hardware accessing the LAN utilizes a six byte hexadecimal MAC address. The first three bytes of this address is reserved to identify the vendor. For example, an iPhone may have an address of E4:CE:8F:C2:9D:AA. The first three bytes E4:CE:8F identifies the vendor ‘Apple’ and it is likely that thousands of other iPhones start with the same 3 bytes. The remaining three bytes C2:9D:AA are unique to the individual iPhone.
<<< monitoringMobilePhoneTraffic.png >>>
Nearly a dozen vendors (e.g. Cisco, Enterasys, Exinda, Juniper, nBox, Sonicwall) are now exporting MAC information in their flow exports. Learn how to export [MAC address with Flexible NetFlow] http://www.plixer.com/blog/netflow/getting-mac-addresses-from-netflow-v9/ . Setting up a simple network monitor will help you proactively keep track of this traffic.
If your NetFlow or IPFIX hardware can export Username, you could click on a username and see the number of devices authenticated by the same user.
<<< sonicwall-Ipfix-username.png >>>
Monitoring BYOD traffic is a growing concern and the above report can be run against flow exports from the Cisco ASA, Palo Alto Networks and the SonicWALL (example above). Vendors are always looking for new and innovative ways to filter on this data.
KEY WORDS:
network monitoring
flexible netflow
network monitor
monitoring mobile phone traffic
monitoring byod traffic











Leave a comment