IP Host Reputation
Today, some NetFlow collector vendors are comparing IP addresses found in flows to reputation lists. This host reputation look up process is a routine that goes out to an Internet based reputation list provider every hour and downloads an updated list of known hosts that end systems on the network should not be communicating with. Typically this is a list of compromised hosts that have a reputation for sending nefarious traffic (e.g. C&C).
Read part 1 of this series.
To keep the list as accurate as possible, it is generally updated by several Internet Service Providers and government agencies. Host Reputation is also one of the best detection methods used against Advanced Persistent Threats.
“We’ve learned that NetFlow can tell us who is talking to who across our network, but how can we tell if either who is a bad actor? By checking the reputation of the IP addresses at both ends of the conversation.“ – Mike Schiffman at Cisco
In locations where NetFlow or IPFIX hardware is not available, inexpensive probes can be deployed which provide the insight necessary. By collecting metrics in every corner of the network, MSSPs claim to increase situational awareness which empowers them to make faster, more informed decisions. Some MSSPs are deploying a distributed NetFlow collection solution that can be compared to tapping sugar maples in early spring. By running the sap back to a sugar house and boiling down huge volumes of sap to a manageable size they can utilize the reduction to enhance their visibility into the collective security landscape.
The leaders in MSSP claim that by using flow technologies and implementing best practices they can improve security the posture for customers. By leveraging NetFlow for threat detection, the benefits often include:
- Faster detection times : Mean Time To Awareness (MTTA)
- Improved response times - improving internal support
- Quicker Mean Time To Mitigation (MTTM)
NetFlow in Forensic Investigations
All companies are under attack every day. Just as a retail store can’t stop all shop lifters, neither can the best IT security teams stop all forms of malware from getting into a company. When an exfiltration does occur, flow analysis is often either directly involved with the detection or certainly a significant part of the investigation and reconnaissance effort. NetFlow reporting can provide graphical details that help administrators comprehend the magnitude of an infection. 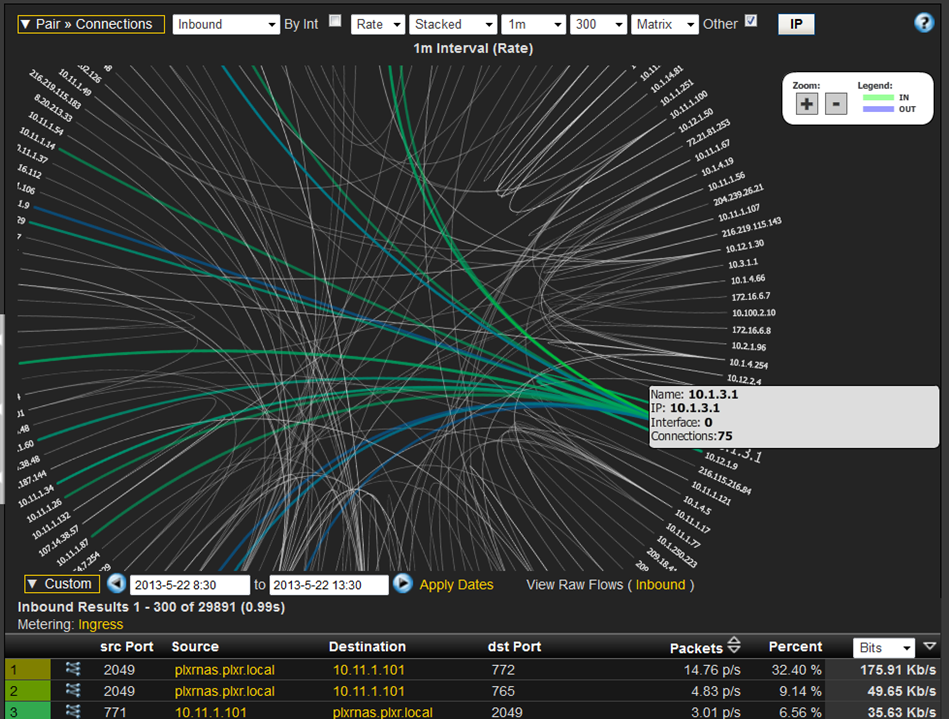
NetFlow Analysis after the infection is also an important function performed by MSSPs. Because most NetFlow collection systems archive data, they prove extremely useful when forensic investigations need to take place. It can be used to answer tough questions such as:
- What was the machines behavior leading up to the problem?
- Who else did they communicate with and are there other machines on the network exhibiting the same behavior.
Summary
Although deep packet inspection continues to be a primary APT detection method, flow technology is without a doubt an ideal additional layer of protection. Packet capture provides greater detail however, it often can’t be done on every internet connection in every remote office. Flow Analysis allows security teams to cover and record all traffic to every location at each customer network at all times similar to the security camera’s deployed in a financial institution. If the traffic entered the company, it was almost always captured and recorded with NetFlow or IPFIX.
Although NetFlow and IPFIX add a great additional layer of protection, MSSPs understand that one of the best proactive counter threat measures is education. This is why some MSSPs make efforts to educate the customer’s employees on topics such as:
- Why they need to make sure best practices are utilized when bringing files in and out of the company’s IT infrastructure.
- What spear phishing is and why this isn’t their lucky day and they shouldn’t click on that link
- Why we need to be careful with social networking sites









Leave a comment