What's Missing in NetFlow Threat Detection?
Most NetFlow exports do not include the entire data portion of the packet. Sophisticated threat detection systems require this data in order to compare the contents to a database of signatures.
Can NetFlow Export Packets?
A NetFlow competitor called sFlow exports the entire packet, however its sampling architecture results in frequently missed infected frames. Cisco Smart Logging Telemetry NetFlow technology which is available on the Catalyst 3000 series can export entire packets however, it only exports datagrams that it detected via ACLs. NetFlow-Lite on the Catalyst 4948E can also export entire packets however, in most cases it is configured to sample. The bottom line is that NetFlow and IPFIX collection is not intended for large scale full packet exports. NetFlow does however try to give you 100% of the connection information which can be useful for behavior analysis, but it is still limited.
NetFlow Behavior Analysis systems
Some NetFlow Behavior Analysis systems attempt to detect threats by base lining system behaviors overtime. When a host communicates outside of its normal behavior baseline, its index goes up. If the index goes too high an alarm can be triggered. Because an end systems behavior is constantly changing, the alarm is frequently a false positive.
Certainly NetFlow and IPFIX, but generally not sFlow can be used to accurately detect threats. The point of this post is to educate on why it should only be part of a company's Unified Threat Management solution. NetFlow can be used to accurately detect SYN scans, ICMP redirect issues, DDoS attacks, XMAS scans, etc. In practice, these same algorithms will often also get triggered by legitimate traffic. Experience tells us that IPFIX and NetFlow are ideally suited for accounting and utilization reporting.
Grow Your Internal Threat Detection
Internal threat detection is a growing area of concern in many networks today. Some companies are placing firewalls on backbone links as yet another layer of protection from internal infected hosts. Forrester Research calls for a Zero Trust model where networks are designed from the inside out. "The redesign starts with a black box or network segmentation gateway that can handle high speeds – up to 10G interfaces. The gateway acts like a UTM appliance, but it does much more than provide firewall, antispam and content filtering features. It can add data leakage prevention capabilities, intrusion prevention and encryption to the network" said John Kindervaq, a senior analyst with Forrester Research, Inc. NetFlow is largely about monitoring internal traffic. The Cisco ASA, Palo Alto Networks firewall and the SonicWALL firewall all export NetFlow or IPFIX.
NetFlow's threat detection value belongs as part of a internal UTM effort where potential threats detected are sent to a SEIM which will then look for other messages from appliances witnessing the same behavior of a host. If other threat detection efforts are not detecting the same suspicious behavior perhaps a false positive can be avoided. Here's a thought: maybe the security appliance reporting the bad behavior should have an index whereby its accuracy for detecting legitimate threats could be graded over time.
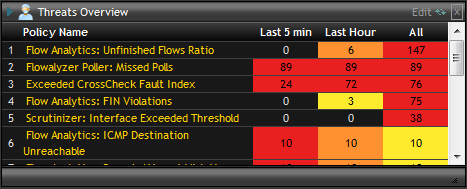
Although often used as a differentiator by NetFlow reporting companies, the demand for dedicated NetFlow and IPFIX threat detection tools is limited. Detecting security threats with NetFlow Behavior Analysis systems is not often the best primary threat protection due to unpredictable host behaviors and lack of the entire packet. The largest opportunity for threat detection with NetFlow lies in IP Host Reputation lookups.
Join NetFlow Developments on Linkedin.










Leave a comment