Detecting Advanced Persistent Threats and other Network Security Threats with NetFlow and IPFIX requires advanced flow analytics. For example Top hosts, top applications, top DSCP values, etc., it’s great information and these reports can be used both reactively and proactively but, it’s just the tip of the iceberg as NetFlow can tell us about all kinds of anomalous traffic that may be flying under the radar.
For example, a host scanning the network causes lots of flows but uses little bandwidth. What if you only want TCP, UDP and ICMP protocols on your network. Would you want an alarm if DDP, DDX, IPv6 or IGMP showed up? Because what we want to see about the network can change per business, threat detection systems need to allow for custom algorithms (e.g. monitoring facebook traffic).
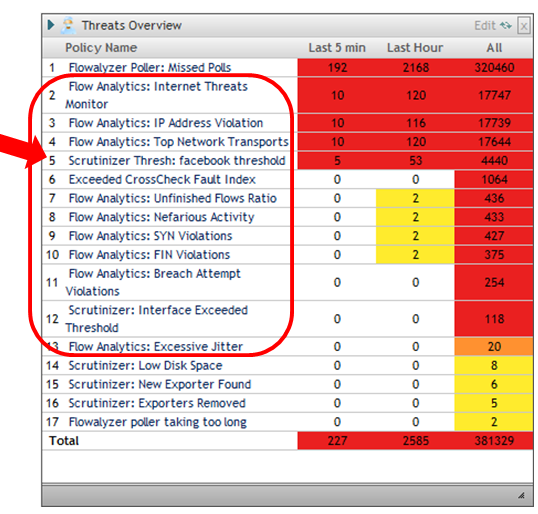
Below you can see a more detailed view of the outstanding alarms with additional columns. The first and last violation time stamps are displayed as well as a way to expand and see all the hosts that have violated each algorithm. Lets drill in on the Internet Threats Monitor.
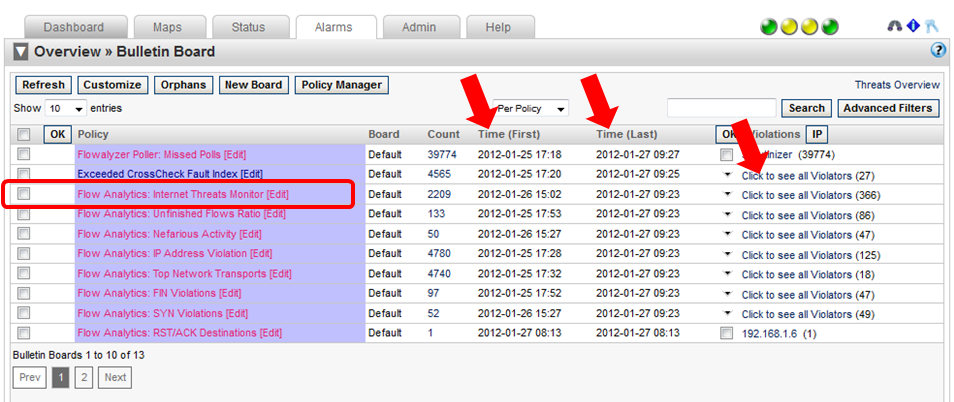
Internet threats is an IP host reputation database that is downloaded by all our NetFlow collectors every hour. This algorithm monitors the source and destination address of each flow to see if it is on the poor reputation list. Positive matches trigger alarms. Here you can click for a menu to gain further insight into the traffic which can help admins be more effective at detecting some Advanced Persistent Threats (IPTs).
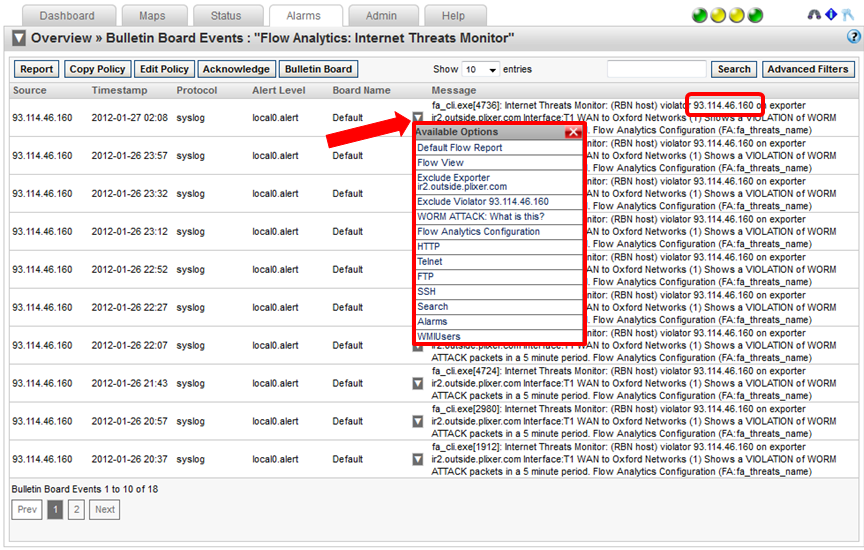
NetFlow and IPFIX Threat Messages
NetFlow and IPFIX are being used by Cisco's Smart Logging Telementry and SonicWALL firewalls to send threat detected messages. Expect vendors to get on board in the coming months as although flow technologies can be used to detect some threats, the lack of the entire packet allows the IPS to maintain its primary position in threat detection and prevention.
The Cisco ASA NSEL also exports messages in NetFlow related to flows violating ACLs. Make sure your NetFlow Analyzer supports these types of exports.









Leave a comment