Unfortunately, businesses that conduct confidential transactions over the Internet should expect hacking attempts and more than likely some will be successful at circumventing the best defenses. Once they are in, how will your team discover them? The answer: you may not be able to.
If an employee connects to the corporate wireless network with a hand held device that is infected with malware and the malware doesn’t attempt to communicate over the network, in many environments it is undetectable. Because of this, detecting malware is a game of sit and wait for communications that expose themselves. Sometimes they do it by attempting to export information to the Internet. What are they trying to steal?
Beyond direct monetary theft, there is also a market for stolen intellectual property. When the stakes are high, paying millions to know what your competitors are doing can provide huge advantages in the market. If the higher ups are paying consultants for competitive market studies, some probably really don’t care how the details are gathered as long as they are accurate and helpful. In some cases, consultants offer a veil of protection from being associated with these types of cyber crime.
To increase the difficulty of stealing information from corporate servers, some IT organizations remove Internet access from key servers. Only temporary access is granted for periodic updates but, the bottom line is that theft has and will continue to happen and when it does companies of all sizes need to ask themselves ‘what will we do’. Many times the answer starts with investigation. To properly look into a possible insurgence, IT needs to have already setup a network traffic surveillance system. In many cases the turn to technology for accomplishing this is flow data. Specifically NetFlow and IPFIX can be used to capture the communication details on all electronic connections in every corner of the network. Good news: all routers, servers and firewalls support these technologies and can send the data off in real-time to a NetFlow collector for future analytics.
Similar to the role a DVR plays for a CATV security system, the IPFIX and NetFlow traffic analysis solution collects and stores the data for real-time threat detection and for future investigations. This also helps with industry compliance regulations. When IT receives a report about something suspicious, they turn to the NetFlow collector to hunt down the problem and uncover all the details. Beyond reactive investigation, how can flow data be used to uncover unwanted network transactions proactively?
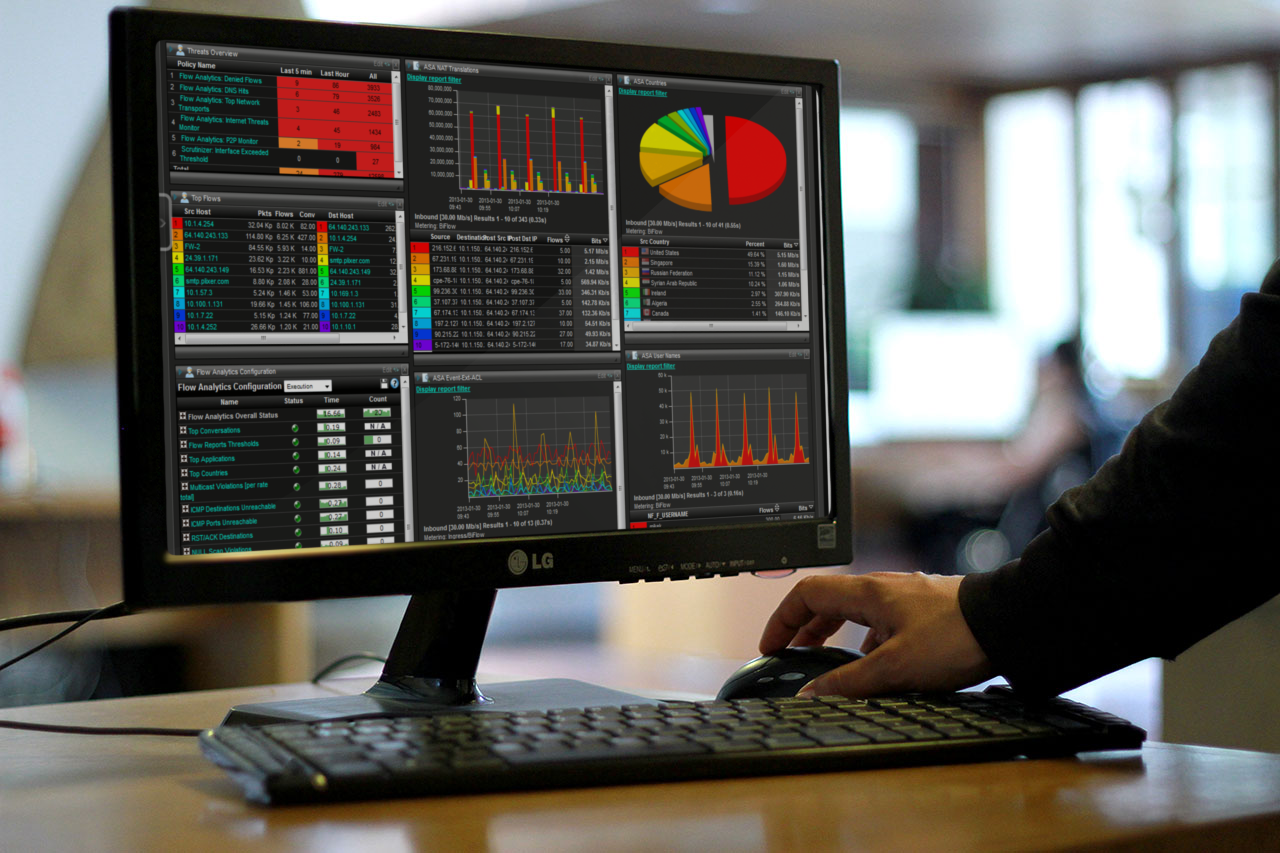
Some NetFlow and IPFIX collection solutions perform flow analytics on the data they are receiving. Flow analytics is comprised of dozens of algorithms that the flows are passed through which attempt to detected suspicious traffic patterns. Some solutions even baseline the flows and compare current behaviors to those in the past. The goal of flow analytics is several fold but, generally the system is trying to uncover:
- Suspicious application traffic to/from hosts or subnets
- Unauthorized devices acting as DHCP servers
- Odd or non-typical TCP flag patterns
- Communication with hosts that have been black listed
- Asymmetric traffic patterns from hosts that shouldn’t be sending lots of data in a particular direction
- Odd flow ratios comparing destination hosts to number of flows
- Suspicious connection durations from hosts unlikely to participate
- Connections indicative of participating in a DDoS
- End systems that appear to be beaconing for a C&C server out on the Internet
- Unusual time of day traffic
- Traffic to or from countries on watch lists
- Other reconnaissance efforts such as low byte volume connections that are repeated over time
- Excessive requests to a specified DNS server(s)
- Abnormal active connections to specified internal servers
- Unauthorized connections from internal servers headed to an Internet address
Check out the leader in NetFlow and IPFIX.









Leave a comment