One of the biggest challenges to traveling has been taking off your shoes and removing the laptops from bags. When
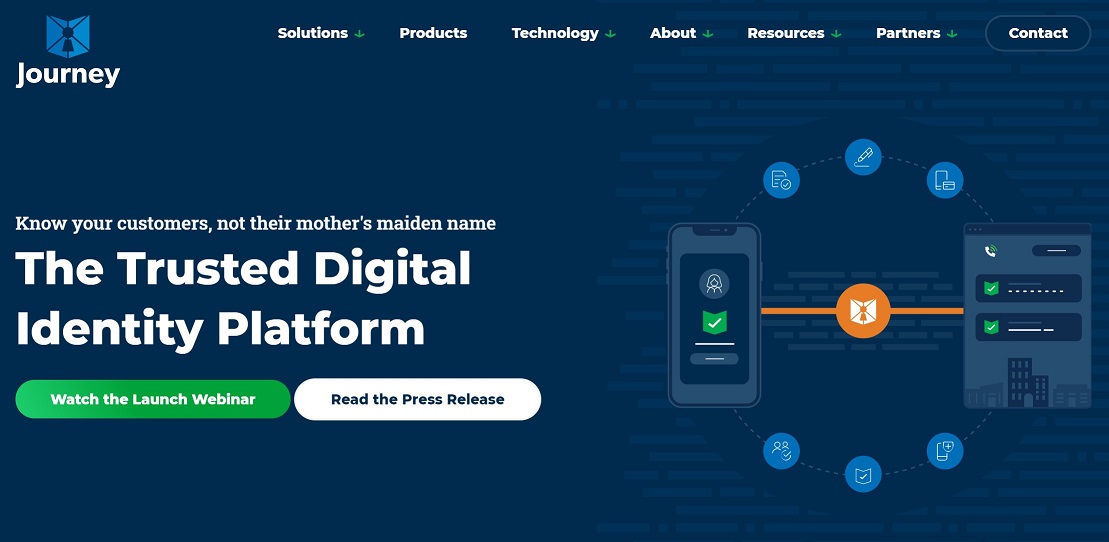
Last summer we broke the news on Journey.ai adding identity and trust to the contact center. The company has just
Now is a great time to launch a secure conferencing solution. Millions of people are working and learning from home
Blackberry, the company once-known for ultra-secure email via phones with superior keyboards was overtaken by Apple and Android solutions in
SonicWall today unveiled an enhanced version of its SecureFirst Managed Security Service Provider (MSSPs) Program to provide the licensing models,
Millions of people newly working at home on computers IT has likely never configured, coupled with hackers dramatically increasing their
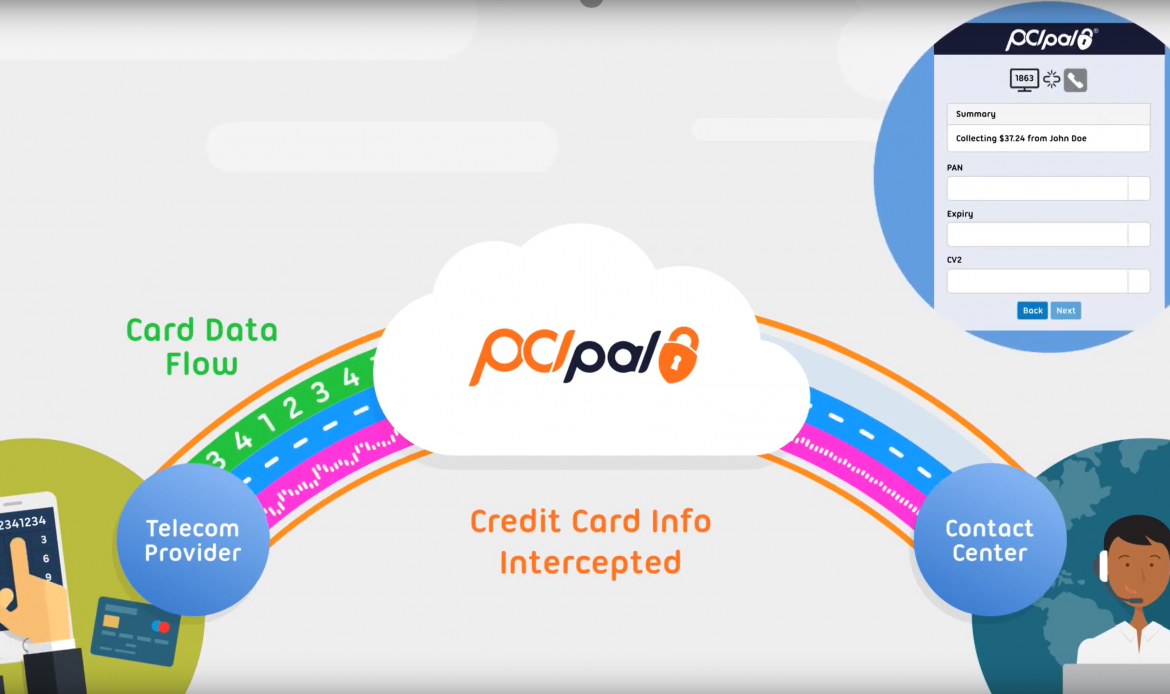
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard designed to create an additional level of protection for card
Physical security in business is obviously less glamorous and scaleable than cloud, cybersecurity or software because it doesn’t scale as
Last year we broke the news on Avant Analytics in our exclusive interview with Jen Gallego, EVP of Channel Sales
Keysight just released their Security Operations Effectiveness survey which was commissioned from Dimensional Research from 307 participants that strategize, architect,