The long-tail, a term coined to describe the ability for organizations to sell vast amounts of products in small quantities accurately describes how a music store like iTunes can generate massive quantities of profit selling virtually limitless inventory.
The online world made this possible. Try as they might, Barnes & Noble could not match the inventory of Amazon in all its stores. Online wins because inventory is near-infinite.
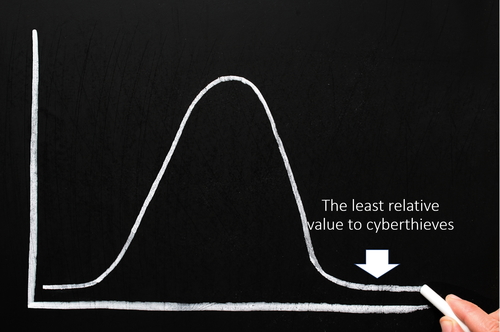
In the cybersecurity world there is is a similar phenomenon taking place. The same bell curve applies but in this case, we can assign it to the value of a target. We are seeing an aggregation of value which by definition increases the focus by cyber-criminals.
Banks were some of the first targets of hacks and to this day remain so but to a hacker, there is also value in data and access.
- Gaining access to IoT devices allows hackers to turn them into DDoS appliances and data discovery tools.
- Gaining access to cloud vendors potentially allows access to all the customers on the cloud.
- Security and networking vendors too are in the heart of the bell curve in terms of the amount of focus hackers will put into attacking them.
- Gaining access to a vertical software/cloud vendor such as Salesforce could expose the customer records of global businesses.
Perhaps the most valuable item of all worth stealing was the OPM database. China hacked it which allowed the government to gain access to incriminating information which could be used for blackmail on over 22.1 million people who at one-time or another were involved with the U.S. government.
Although rarely discussed, this breach constitutes perhaps the biggest threat to the security of the United States.
In this case there was a mismatch between the value of the data and the protection it was under.
The point is, this attack shows that there will be an increasing amount of focus on targets of great value. The challenge is, the level of security which can be applied to such targets has limits. A determined attacker will always get through… This is why anomaly detection is crucial in all networks worth protecting.
Another case in point is the recent hack of a FireEye researcher in Israel. A FireEye spokesman confirmed data had been stolen from one its employees, but said there was so far no evidence that the companies’ systems were affected. This statement is not as reassuring as we would have liked. FireEye is at the top of the list of high-value targets and hackers will use whatever vectors they can to get to their data.
This gets us to the long-tail as it applies to cybersecurity. All things being equal, high-value targets will grow in value based on the network effect. The more customers a router vendor has, the exponentially more value there is to an attacker as these routers are spread throughout networks and give access to even more connected systems – PCs, servers, sensors, websites, etc.
If we follow this out to its natural conclusion – endpoints could become relatively safe compared to the cloud and other vendors companies rely on to keep them safe. The ones enumerated above.
The reason is quite simple… As the value of these central treasure-troves grows at an astronomical rate, the ability to secure these resources cannot. You eventually run out of security options to apply to the network.
The move to everything-as-a-service has not slowed down one iota but if anything can deter its rapid ascent it will be the acknowledgement that all systems are fallible and eventually the highest-value ones will be breached. At this point, the long tail of cybersecurity will be evident and there may be a move back to securing data as locally as possible.