We recently covered the topic of election cybersecurity and offered suggestions on what political parties can do to stay secure. As a nation obsessed with Russia and election interference for over two years, one might imagine the election cybersecurity of the United States would be second to none. After all, the U.S. leads in so many areas of technology – including cybersecurity, shouldn’t the nation’s election infrastructure take advantage of these advantages?
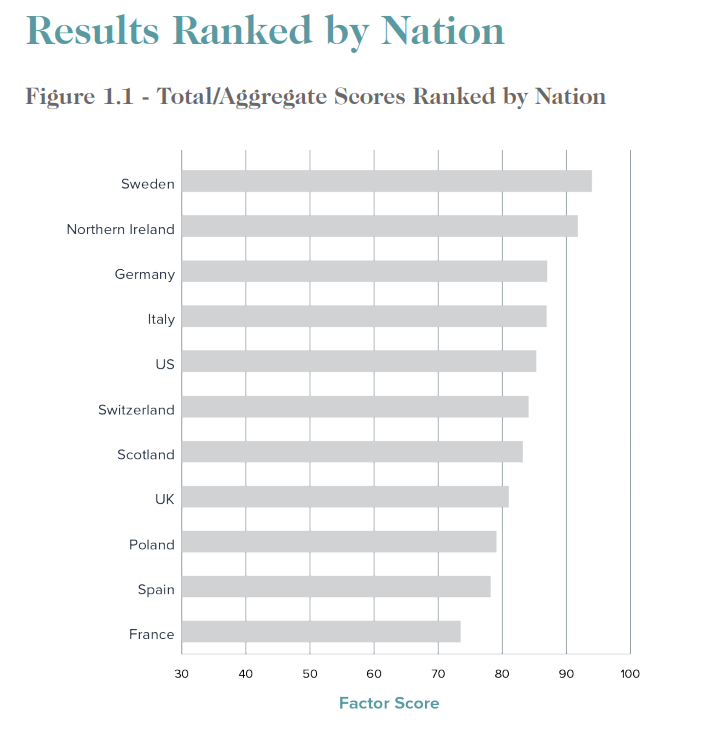
SecurityScorecard has just released (PDF) international cybersecurity rankings of numerous nations and the U.S. ranks number five behind Sweden, Northern Ireland, Germany, and Italy. It beats Switzerland, Scotland, UK, Poland, Spain and France.
There are few if any bright spots for the U.S. – it ranks eighth on DNS security ahead of just Switzerland, Scotland and France. It ranks seventh on network security.
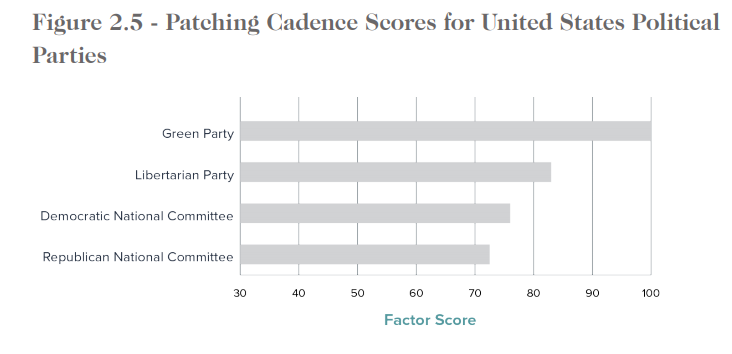
Worst of all – by far, is patching cadence. The U.S. ranks sixth here! Patching is the low hanging fruit of cybersecurity – it is astonishing how poorly the country ranks here.

After the last election where the DNC was hacked and John Podesta fell for a phishing attack, one might imagine the Democratic National Committee would be doing much better. Even if it has improved, DNC, organizational behavior still lags far behind.
SecurityScorecard researchers did notice usage of Okta, a two-factor authentication tool, by the DNC. However, in one instance, the initial URL of a calendar application utilizing 2FA is served unencrypted over HTTP. A motivated attacker could MitM (Man in the Middle) the beginning of this session, redirecting the calendar authentication to a bogus instance of Okta, harvest the user’s credentials and still send the 2FA mechanism as normal. It is very possible the end user would have no indication their credentials were just taken from them.
The RNC is utilizing the content delivery and internet security company, Fastly, however there are some instances where the integration and configuration are not sound as it applies to DNS health. Additionally, they are leaking ArcGIS (a popular mapping software tool) administrative subdomains where projects for a certain state can seemingly be gleaned. Finally, a completely unencrypted login to what appears to be a RNC-API server was quickly discovered as well.
Additionally, a major U.S. political party was programmatically leaking a voting validation application, which enumerates voter name, date of birth and address via search terms. SecurityScorecard has already disclosed this vulnerability to the appropriate parties.
The biggest challenge for political parties is the culture of cybersecurity – if you aren’t patching quickly, you aren’t taking security seriously. The other areas of this report are important as well – it all is. A determined adversary can almost always get in. Especially now, that this report is out and they know where to attack!

It’s time to take cybersecurity seriously and fix the problem areas and move to the number one spot.
We recently went into depth on the problems of election cybersecurity as well as the solutions. Feel free to study our thoughts and contact us if you have questions or need assistance.






