It’s a good time to be in the Cybersecurity business.

Quite often, highly secure computers are disconnected from the outside world so as to not get hit by hackers. However, it seems these air-gap networks named for their isolation from other computers are not as secure as we once thought. A hacker can get to these networks in the following manner. They design software which logs the keystrokes and subsequently transmits this information via FM radio signals generated by the graphics card – without changing the display so the user doesn’t detect the attack. These signals are then picked up by a nearby cellphone (obviously equipped to pick up radio signals which many are) that can subsequently transmit this data anywhere. In this case they used a Samsung galaxy S4 and had to plug in the headphones to get the radio receiver to work. Since FM radio signals travels great distances, through walls, etc. this is a great way to tap into highly-secure computers.
Prof. Yuval Elovici, the head of the cyber security research labs at Ben-Gurion University in Israel discusses air-gap security as well as the latest threats and developments. At 14 minutes is where the discussion relates to what is written here.
Here is the challenge though; you have to install this malware on the computer in question. A simple way to do this is to plug in a USB drive. Obviously this attack vector is not as easy to execute as sitting at home in your pajamas and running scripts across a massive number of servers – hoping to find a vulnerability. This type of attack is much more targeted – like spear phishing which goes after specific individuals or groups by potentially posing as a friend or acquaintance or using otherwise personal information to make the target more likely to take the desired action such as clicking a link.
See AirGap malware in action
To make this play out in the real world, you could bribe a member of the cleaning crew. Other threats could come from a malicious insider or a careless employee who receives a USB device at a conference, in the mail, etc.
This is said to be how the Stuxnet worm got onto Iranian computers many years ago.
In other words, this is more a Mission Impossible type of attack but air-gap networks are likely worth the trouble for the right malicious actors.
Here is the current range of the AirHopper vulnerability in a building where a computer is plugged into the conference room – potentially a less secure part of a secure building. A cell phone would have to be in this circle for this attack to work.
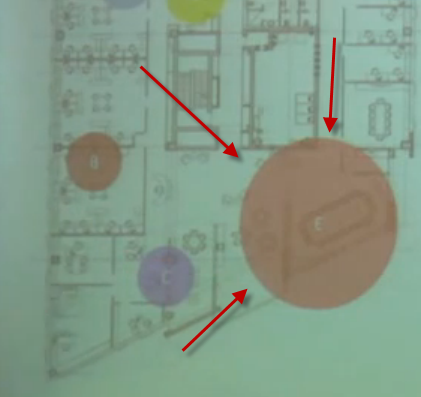
In the above demonstration, AirHopper malware is transmitting data between 13-60 Bps at a range between 1-7 meters. It is unclear how far these FM signals can travel but the professor did explain they travel farther when carried over a longer cable than a shorter one. So a computer connected to a projector makes an ideal target.
Here is the reality of cybersecurity… You have to worry about physical security as well as virtual and there is no such thing as a network which is 100% secure as long as there are smart people looking to break-in. It’s a good time to be in the Cybersecurity business.
H/T: Bloomberg





